I.INTRODUCTION
Intelligent network slicing is a technique used to optimize the performance of vehicle-to-everything (V2X) networks. It involves partitioning the network into multiple virtual networks, each of which is designed to handle a specific type of traffic. For example, one virtual network could be optimized for high-bandwidth video streaming, while another could be designed to prioritize low-latency communications for safety-critical applications. The connectivity needs are ever-increasing, so it is demanding rapid action toward consideration of the network capacity in the existing infrastructure, especially with the advent of the Internet of Things (IoT) [1]. Every few years, new technology emerges and adds traffic to the network. For instance, intelligent transportation systems have emerged recently and are focusing on making autonomous cars ubiquitous. This entails the connectivity demands from millions of sensors for context-aware driving [2]. This type of intelligent transportation falls into the category of V2X communication [3]. The system resides on multiple sub-communication networks like vehicle to vehicle (V2V), vehicle to network (V2N), vehicle to infrastructure (V2I), and vehicle to pedestrians (V2P) [4]. In the last decade, V2X networks have been capturing the interest of researchers in the domain of IoT and communication systems in general. The widespread of such sophisticated systems is seen as a landmark that will transform the future of vehicular networks for good [5]. V2X networks offer safe roads, efficient transportation, and many side applications are expected to emerge [6].
At present, the V2X networks comprise two types of technologies: the vehicular networks based on Dedicated Short-Range Communication (DSRC), which is founded on IEEE 802.11p and IEEE 1609.1.4 standards, and those based on the vehicular cellular networks such as long-term evolution (LTE) [7]. DSRC has long been seen as the only V2X technology; nevertheless, identifying the associated limitations and drawbacks, including the coverage, latency, and insufficient throughput and data rate, made the development of advanced and more sophisticated networks inevitable [8]. The higher throughput and data rates enable the development of heterogeneous networks (HetNets) that allow large coverage cells (LTE-Macrocells) as well as small coverage cells (direct link communication DSRC). The LTE macrocells help attaining higher throughput rates and wide coverage by having access to a large bandwidth in the applications like infotainment. The small cells meet a short range and direct coverage [9]. LTE cells can be used to broadcast priority signals using direct DSRC (short coverage) for transmitting information related to road safety conditions, such as accidents or giving way to ambulances to keep neighboring vehicles aware [10].
The capacity of V2I links and the underlying ultra-reliability requirements are catered to through the ergodic capacity of these networks while ensuring reliability across all links. The channel dynamics emanating from higher speeds depend on spectrum sharing efficiency, allocation of power, and catering to the large fading effects in a channel [11]. This shifted the focus toward using cellular communication networks called C-V2X [12]. This standard entails communication enablement across individual V2X entities like V2V, V2I, and V2P. In 2017, a bi-air interface was used, which includes a wide area network and a direct communication interface. The focus here was to ensure enhanced road safety mechanisms through awareness messages and decentralized notifications [13].
Fifth Generation (5G) networks are seen as the potential enablers of such V2X communication networks having the innate ability to meet the high throughput and low-latency demands [14]. HetNet is one of the 5G network topologies which contains multiple radio access technology (Multi-RAT) in the same network, as shown in Fig. 1. This scheme is considered to be a fundamental one while addressing networking slicing. The network slicing view differed from the users’ and network administrators’ perspectives. In the former, network slicing refers to using different RAT for meeting specific user needs, including V2X and safety. In the latter, network slicing refers to the user some RAT for massive machine-type communications (mMTC) applications, RATs for ultra-reliable low-latency communications (uRLLC) applications, and RATs for enhanced mobile broadband (eMBB) applications [15]. Massive machine-type communications RAT high-density connectivity requirements, including some specific applications in urban areas, etc. uRLLC RATs are used for low-latency and high-reliance communication, including autonomous driving. eMBB RAT is used for infotainment and other high-bandwidth application.
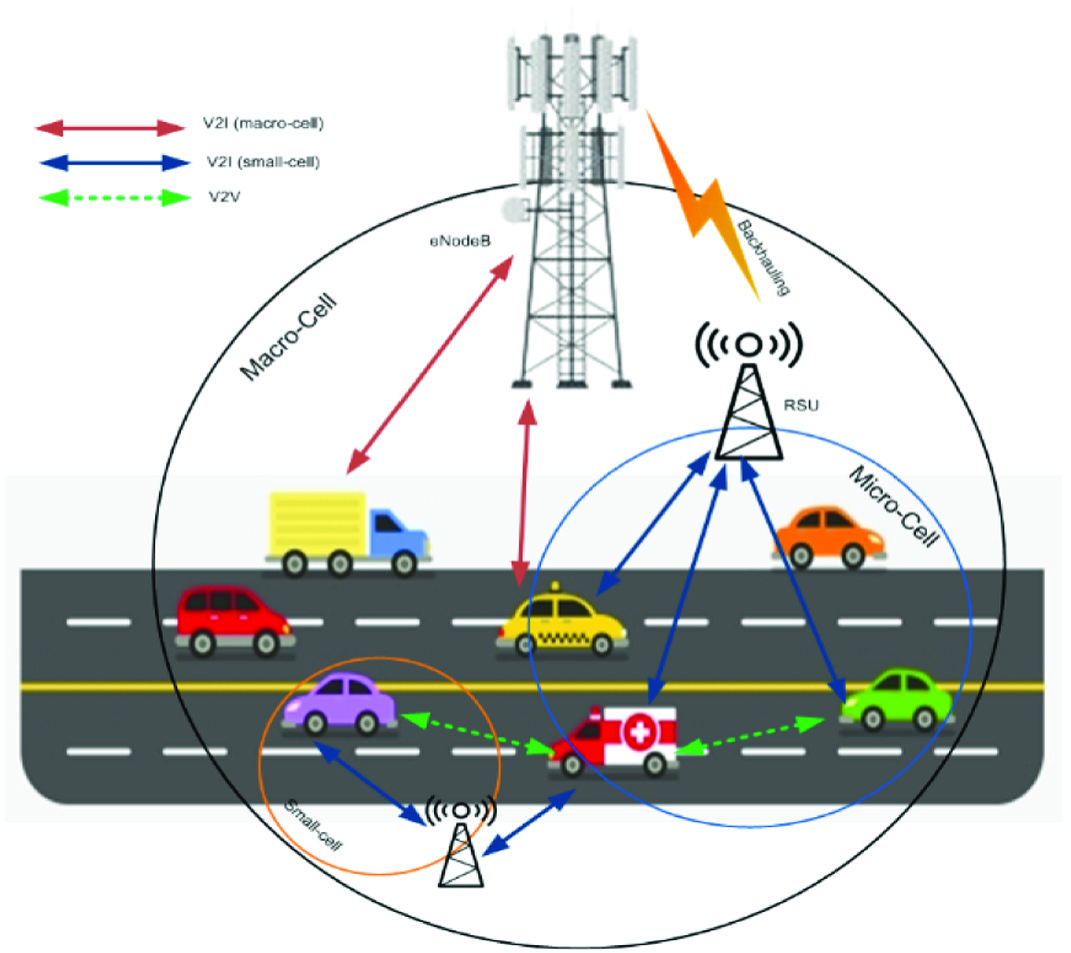 Fig. 1. V2X HetNet configuration.
Fig. 1. V2X HetNet configuration.
With the increase of HetNets, the network control and management demands across the base stations also increase [16]. Additionally, the controller must address vehicle control demands, which can be managed through software and flexible networks.
Although a plethora of benefits is offered by the software-enabled V2X networks, the control and modeling of such network slices are highly complex. A typical slice of network demands meticulously worked modeling of the existing network and taking timely decisions [17]. Therefore, using intelligent and autonomous systems that rely on self-learning and decision-making becomes indispensable. To cater for such issues, machine learning (ML) algorithms are commonly used and reside on an underlying AI scheme. These systems contrast the traditional modeled networks, where a system designer needs to manually incorporate all the parameters to create network slices [18]. The ML methods such as deep learning (DL) and neural network can learn dynamic network parameters and make predictions based on available information while incorporating past events and learned parameters. These methods are widely used in network applications such as data analysis, network congestion analysis, and resource management [19]. Using existing methodologies and tailoring their use in V2X communication are expected to be a highly efficient network slicing technology.
ML’s popularity in network slicing is due to its ability to extract patterns and features from complex network structures and parameters [20]. Various ML/DL algorithms shall be used, which are trained initially on the general network conditions and later used for making the allocations on their own. Additionally, they encompass RL, where the system dynamics are continuously changing. Therefore, a static ML algorithm that has been exposed to only a finite set of conditions cannot perform efficiently [21].
This study reviews V2X slicing using a proposed taxonomy that describes enablers, configurations, requirements, and ML/DL algorithms. The study is structured to target various schemes of comparison, including networking, the network slicing schemes in general, and a comparison between their use and limitations, followed by a comparison of the use and benefits of ML techniques in network slicing. Related survey papers are summarized in Table I.
| Ref./Year | Slicing | ML/DL | Specifications | Taxonomy | Requirements | End-user of V2X perspective | Industry of V2X perspective | Focus |
|---|---|---|---|---|---|---|---|---|
| [ | URLLC (Edge computing) | |||||||
| [ | URLLC (Edge computing) | |||||||
| [ | Safety in C-V2X | |||||||
| [ | Security | |||||||
| [ | V2X motion planning | |||||||
| [ | eMBB applications | |||||||
| [ | mMTC | |||||||
| [ | ML | Security | ||||||
| This survey | Slicing in V2X |
The surveys revised in this paper are classified into two groups based on the V2X perspective. The first group is the end-user perspective, and the second is the industry perspective. From an end-user perspective, such as in [22–24], security and safety are the two metrics of concern using ML algorithms. In [24], ML algorithms have been provided for network slicing in V2X. In [22], these networks are reviewed under safety consideration with the help of software-defined network (SDN) controllers.
The study by [23] investigates the ML algorithms under security measures under their application to the SDN controllers. The works in [25–29] take an industrial outlook and determine the control mechanisms under network requirements, including the eMBB, mMTC, and URLLC. To meet the URLLC slicing needs, [25,26] provides the use of mobile edge computing (MEC). These algorithms help decreasing the latency across the edge vehicles and help in lowering the capacity across the cellular BS. The work in [27] takes a perspective of motion planning in V2X instead of slicing. It uses the ML to the SDN in the context of autonomous vehicles. Bandwidth awareness is the work concern in [28] to provide vehicles with efficient spectral efficiency. In [29], Implementing 5G in vehicular networks has potential for increasing capacity, data rate, coverage, and device mobility. These studies’ limitations are that they focus on only one slicing area. There is no comprehensive review that discusses the V2X slicing in all directions. Thus, the contributions of this study are as follows:
- •To the best of our knowledge, this is the first survey that deals with applying ML algorithms in V2X slicing based on the network requirements from a dual perspective.
- •This paper discussed techniques for network slicing in conventional and machine learning approaches in V2X networks and the limitations identified by providing a proposed taxonomy.
- •Also, it explores and describes some challenges with possible solutions in applying these algorithms, like the availability of datasets and security issues in applying ML algorithms in V2X slicing.
- •This paper derived some open issues and future directions in V2X slicing based on ML algorithms like low computation process techniques, datasets collection, and controlling slicing.
The structure of this survey is organized as follows. Section II presents a taxonomy proposed for the V2X slicing based on enablers, requirements, configuration, and ML/DL algorithms used. Section III provides some challenges and solutions to applying ML in V2X slicing. Section IV discusses the open issues and future directions of V2X slicing. Finally, a summary of the review and the article is concluded in Section V.
II.V2X SLICING TAXONOMY
V2X slicing is a type of network slicing that is designed to support communication between vehicles and other entities in the transportation ecosystem, including pedestrians, infrastructure, and other vehicles. The taxonomy of V2X slicing typically includes the following categories:
- •Radio Access Network (RAN) Slicing: This type focuses on the radio interface between the vehicle and the infrastructure, including base stations and roadside units. RAN slicing enables the operator to allocate radio resources such as bandwidth, power, and frequency bands to different V2X use cases based on their specific requirements.
- •Core Network Slicing: (also called (Service/Application Slicing)) focuses on the higher layers of the V2X network stack, including the application layer where specific services or applications are hosted. This slicing type enables the operator to allocate resources such as compute power, memory, and storage to V2X use cases based on their specific requirements.
- •Context-aware Slicing: This is a more advanced form of slicing that considers the context of the V2X communication, such as the location of the vehicle, the type of service/application being used, and the level of security required. This slicing type enables the operator to allocate resources dynamically based on the changing needs of the V2X communication.
Overall, the taxonomy of V2X slicing provides a framework for creating and managing virtual networks that can be optimized for specific V2X use cases, enabling operators to provide more efficient, reliable, and secure V2X communication services.
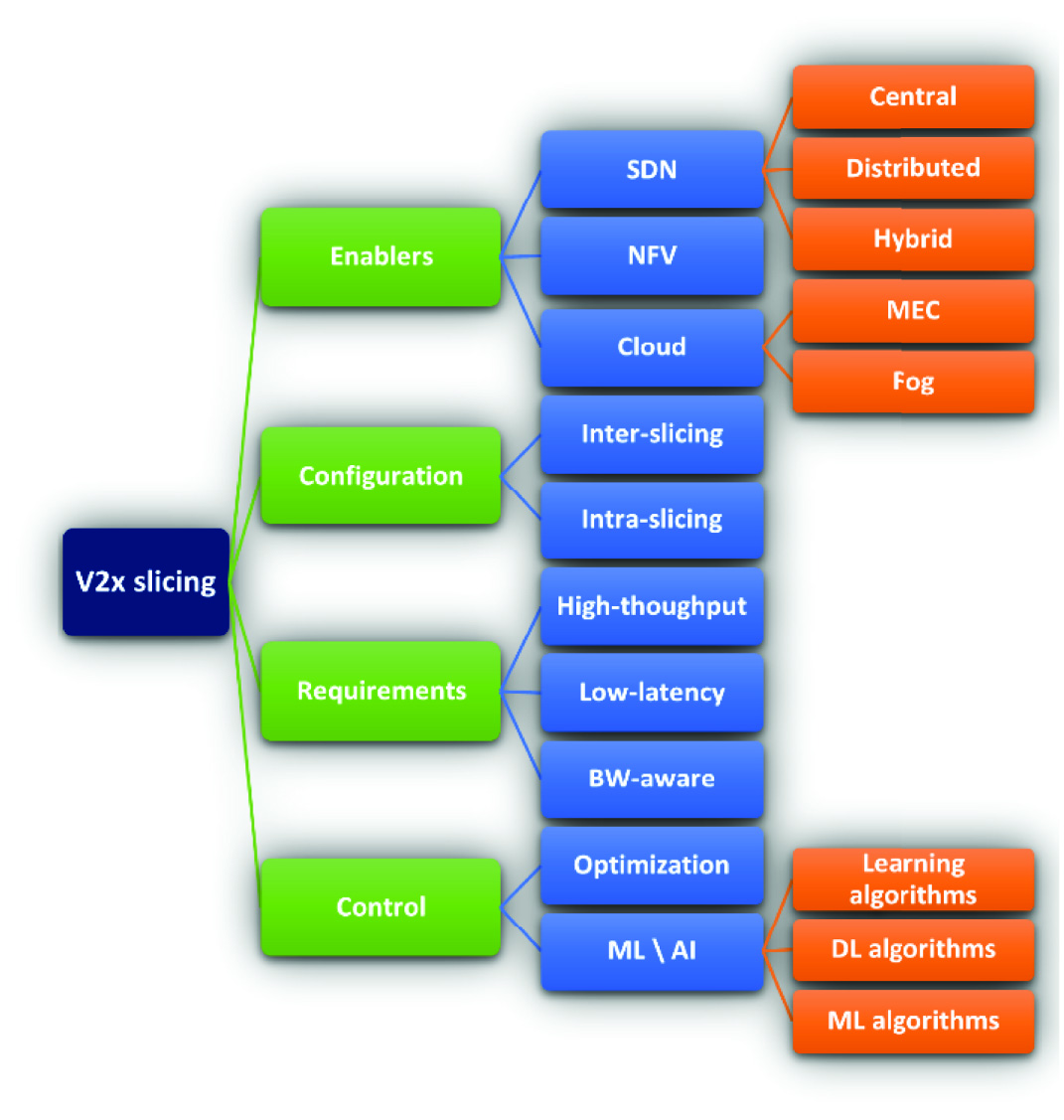
This section elaborates on the V2X slicing taxonomy presented in Fig. 2, where a focus is gradually steered toward using ML algorithms for control and management. The approaches presented in taxonomy generally depend on the enablers techniques like SDN controller, network function virtualization (NFV), and cloud computing. The purpose of using ML is to enhance their performance and give them a competitive edge. Thus, ML/DL can play a role in enabling or assisting with network slicing technologies. By taking a holistic view of the network and using a dataset approach. Also, ML/DL can help determine actions to be taken within the network. The second element presented in the taxonomy is the two tiers of slicing, that is, inter-slicing and intra-slicing. Keeping these configurations under review allows taking decisions and actions based on ML. The third focus on the taxonomy is the underlying parameters, including latency, throughput, and bandwidth requirements for slice creation.
Thus, the presented taxonomy is an all-encompassing baseline for furthering the V2X slicing discussions. A one-stop review is provided to the readers in the context of V2X slicing and enabler while enabling them to apprehend the right enabler choice in a particular system design.
The inter- and intra-slicing configurations will be leveraged using the appropriate ML algorithm. The general requirements in V2X are the slicing based on the throughput, latency, and bandwidth requirements, which have been discussed in this review article.
A.Enablers
This section discusses the operational network slicing enablers in V2X. The review article aims to compare and analyze various ML-enabled network slicing methods for V2X. However, reviewing the networking slicing techniques in the V2X domain and their significance is essential, highlighting the need for intelligent slicing [30].
The widespread use of mobile and portable devices has led to a growing demand for connectivity. Enhanced LTE and 5G resources are being used to meet this demand, which provides efficient networking allocation and division requirements [31]. Higher connectivity and lower latency rates are driving the need for a transition to 5G networks.
However, limitations make it challenging to meet these requirements fully, and upgrading hardware is expensive and not always feasible for large-scale networking needs [32]. SDN & NFV techniques have shifted toward software-based optimization, reducing the need for physical layer resource upgrades. These complementary methods enhance network scalability and flexibility, leading to network slicing methods for IoT networks, mobile communication, and V2X networks [33]. Another method is Robert as a Service in a cloud computing environment, which uses web service as the communication standard to connect IoT and robotic devices to the environment [34].
The work in [35] provides one such study where different factors have been incorporated in creating slicing. These factors involve the available nodes, the scope of slicing, slicing management, and the similar underlying provision to control these technologies through SDN and NFV.
The study entails a comprehensive network slicing method that targets different areas of a 5G network where slicing has been implemented. Along with these, enabling technologies that can meet these models have been presented. 5G Network Slicing Use Cases with Enabling Techniques (5G-NSUE) have been developed with the aid of SDN and NFV techniques running on top of the 5G infrastructure to create slices under different use cases. With the aid of a service layer, network slice layer, and resource layer, the method provided a novel taxonomy of incorporating use cases in the SDN and NFV approach employed.
In [36], SDN was used for network slicing, focusing on the fair allocation of available network resources. The approach used a vectorization method that followed a bi-path approach, distributing resources fairly and optimizing user satisfaction to increase efficiency. Congested resources were identified, and ordered weighted averaging was used for aggregation, optimizing the system’s efficiency and network slicing.
The work in [37] involves a latency-driven approach to address slicing requirements in 5G networks. The approach uses a multi-network tenant system to provide slices based on service-level agreements. Network resources are dynamically provisioned to ensure desired throughput levels using probabilistic methods based on Markov chain models. This approach allows for reducing latency through SDN decentralization.
V2X employs a central SDN in its network configuration, enabling simplified routing algorithms for traffic management and control [38]. However, latency is a concern during high-traffic periods, and communication between users on edge and the central SDN takes longer. This distributed framework increases complexity, but hybrid SDN controllers can be a solution. This involves a central SDN controller and distributed SDN controllers managing some network slices, reducing signaling needs and improving management response, particularly for vehicles across the edge by leveraging short-range communication [39].
Using demand-based control and management with cloud computing as the third V2X enabler can provide a solution. A cloud-based framework on top of SDN can combine network slicing architectures for edge and remote clouds. The edge cloud provides low-latency communication by hosting services near vehicular control equipment, similar to a macrocell [40]. V2X networks operate like cellular networks, with vehicles receiving services within specific macrocell regions. ML algorithms control these edges and allocate resources based on inferred requirements. A remote cloud centrally controls resource allocation, but a potential limitation is lower throughput rates from the central SDN or remote cloud.
The work in [41] proposes using fog computing, which renders MEC computing speeding up data transfer from the edge user to the central cloud, increasing the system throughput. Table II summarizes some of the related works in the V2X slicing enablers.
Table II. Some related works for slicing enablers
| Ref./Year | Enabler | Control | Method | Limitations | Computing |
|---|---|---|---|---|---|
| [ | SDN + NFV | 5G-NSUE | Virtualization | Network Operator Required | Off-demand |
| [ | NFV | User Satisfaction Report | Fair Resource Allocation | Complex Computations | Off-demand |
| [ | SDN | Markov Chains | Resource Allocation | Poor dynamic handling | Off-demand |
| [ | Cloud | MEC | Reinforcement learning | Lower throughput than the main cloud | On-demand |
| [ | Cloud | Fog | Virtualization | Increase in hardware requirements | On-demand |
B.CONFIGURATION AND REQUIREMENTS
The V2X slices are analogous to several physical slices used for handling data originating from different terminals. This is known as inter-slicing and is determined by the determined priority agreements by the network providers [42]. For instance, the data originating from an ambulance, as shown in Fig. 3, shall be handled by the relevant slice configured to manage priority signals. Similarly, the data originating from a traffic light are handled by network slices with wider bandwidth handling due to the dense sensing conditions [43], and the data originating from the traffic will be handled by the inter-slice responsible for vehicular communication. Finally, if the network traffic originates from the mobile terminals, the inter-slice is related to the mobile applications. The number of slices can be selected as desired by the network provider and the requirements [44].
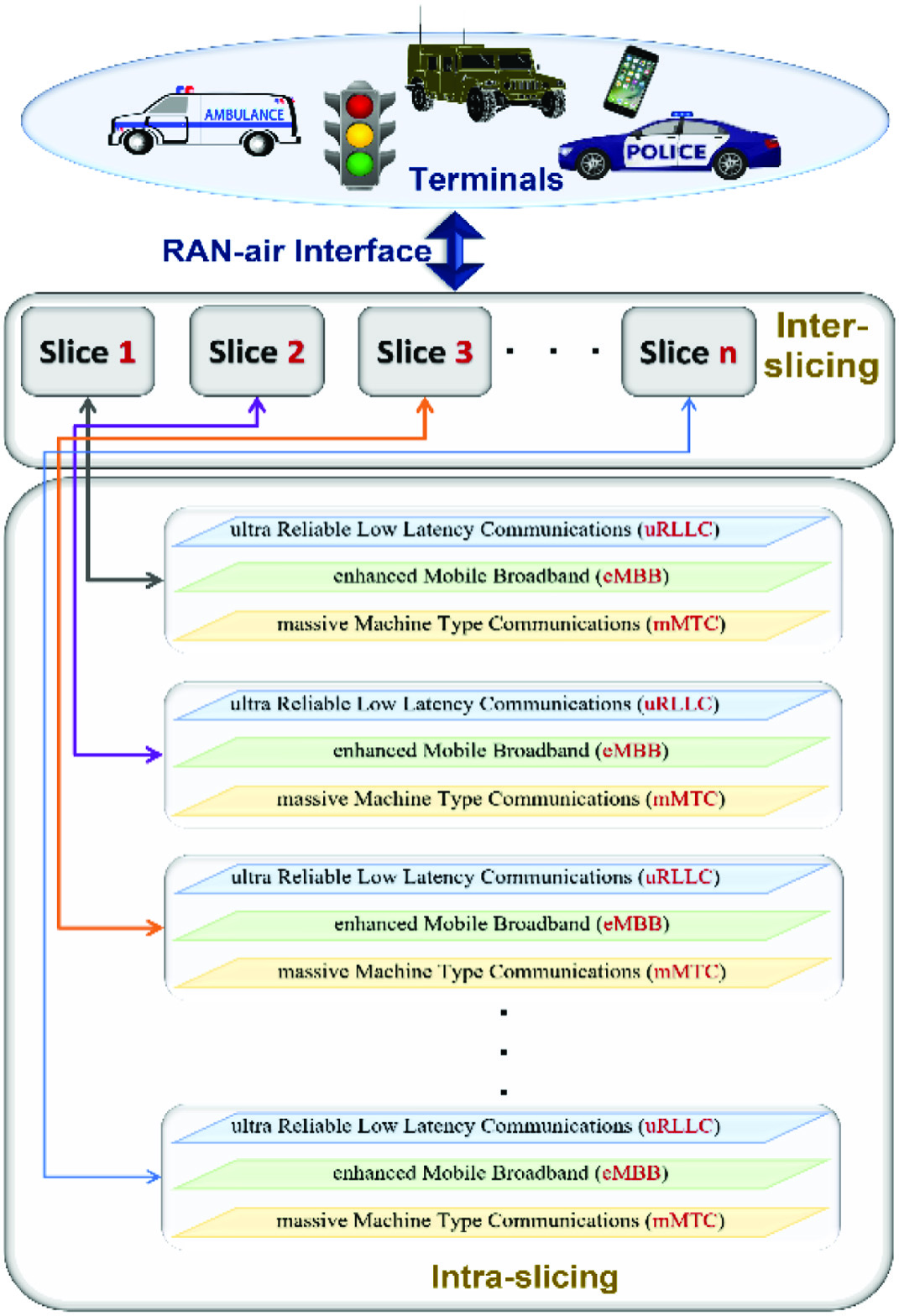 Fig. 3. Inter-slicing and intra-slicing configuration.
Fig. 3. Inter-slicing and intra-slicing configuration.
Each inter-slice is comprised of intra-slices. In an inter-slice, the intra-slices represent the sub-slices that cater to the signal transmission requirements. For instance, an inter-slice intended to serve as vehicular slices will have sub-slices (intra-slices) configured for different applications, i.e., no interference between users in the same slice [45].
The bandwidth-aware requirements can be originated from many sensors, including the high signal processing demands. Such requests are handled by the mMTC intra-slices [46].
Many articles provide details on the slicing configuration in the V2X communication system where ML and DL-based enablers are used. For instance, in [47], the combination of NFV and MEC has been coupled to generate intra-slices intended for users across the edge. Reinforcement learning has been employed as a control parameter for creating intra-slices. Resultantly, the resources are conserved, offering higher resilience against network collapse.
The work in [48] uses reinforcement learning to cater for the bandwidth-aware SDN-enabled network. This configuration fits well for the control of large-scale IoT networks with hundreds of signals. The method enables the optimal configuration of the underlying slicing parameters, including the power requirements, energy efficiency, reliability, and spreading factors. The DL-based controller simulation has been demonstrated in [20]. The use of deep reinforcement learning has been used for the allocation and management of resources. These involve the radio resources as well as the priority configurations across slicing.
The use of reinforcement learning can also be employed in the context of inter-slicing management and control [49]. The decisions related to the allocation of resources across the slices are incorporated through a real-time adaption scheme based on the feedback. This ensures improved service quality. Another method found in the context of inter-slicing is using the Q-Learning Algorithm, as presented in [50,51].
In [50], Q-Learning is presented in the context of radio resource management (RRM) to ensure fair distribution across slices while minimizing the inter-slice influences. In [51], it uses bandwidth allocation in inter-slice relatively rapidly.
The study in [52] finds that Starlink offers comparable throughputs and latencies to traditional fixed and wireless technologies and outperforms commercial Internet access using a geostationary satellite. At the same time, a hybrid approach has been presented in [53] for creating inter and intra-slices. This uses the Q value-based deep transfer reinforcement learning to find the best ratio selection for two slice types using the throughput and latency measures. The delay improvement is 21.4% in the URLLC slice type, and throughput is improved by 22.4% in the eMBB slice type. Table III summarizes related works for slicing configuration and requirements based on ML/DL algorithms.
Table III. Related works for slicing configuration and requirements
| Ref. | Enabler | Configuration | Controller | Requirement |
|---|---|---|---|---|
| [ | NFV+ MEC | Intra-slicing | RL | eMBB |
| [ | SDN | Intra-slicing | TRL | uRLLC + mMTC |
| [ | SDN | Intra-slicing | DRL | uRLLC |
| [ | SDN+ Cloud | Inter-slicing | DRL | eMBB |
| [ | SDN | Inter-slicing | QL | uRLLC |
| [ | SDN | Inter-slicing | DQL | mMTC |
| [ | SDN | Hybrid | QDTRL | eMBB+ uRLLC |
C.Control
In the V2X networks, two controlling methods are adopted, similar to the slicing control methods: optimization and ML algorithms. Amongst these, optimization-based methods are more traditional and have been used for a long. The aim is to attain optimized performance levels under certain limitations. The computational requirements of these methods increase with the increasing network size. For instance, the Heuristic technique is a commonly employed method. Some underlying models in this scheme include Game theory, graph models, Markov Models, and Genetic Algorithms. The work in [54] employs the Markov model for the V2X slicing. The evaluation is performed in a multi-tenant scenario across the urban and rural macrocells to delineate the RRM’s impact.
In [55], the Graph theory model is used for dynamic slicing. The simulation focuses on the use of a two-step method for the construction of the slices.
At first, a time division duplex decides the activation of slices at a particular time. During the second step, resource allocation across the network is made accordingly. A simplified model compared to the two-step model has been presented in [43] using the Genetic algorithm. This optimized model used a single step for inter-slice resource management. The aim is to curtail the number of vehicles that have not gained the required bitrate for communication requirements fulfillment. This enables resource allocations without prior knowledge of the network conditions—however, the computational load increases.
Game theory is the most commonly employed model. The work in [56] uses the dynamic sharing mode in network slicing, where inelastic users are supported by vehicles with minimum data rate requirements. The dynamic slicing mechanism presented in the work offers the same performance as static slicing using game theory, enabling the network to meet mobility requirements dynamically.
The work in [57] develops a one-to-many matching game theory while using the slices’ isolated characteristics. This reduces the interference across and among the micro- and picocells. The simulation results are shown to be dependent on the intra-slicing configurations. The work in [58] depicts NFV as enabling technology and game theory to optimize controllers for eMBB slices in dense networks. Researchers are turning to intelligent systems, such as ML and RL algorithms, for network slicing in highly dynamic systems. RL is typically used for policy-based slicing based on Markov models, allowing for customized slicing policies that overcome dynamic network conditions. This renders the development of a non-linear reward function that is efficient compared to the conventional methods used in [21,59]. Table IV shows related works using AI algorithms as a V2X slicing controller. Some of the most recent ML/DL constraints in the V2X slicing controller will be presented:
- •Limited Training Data: ML/DL algorithms require high-quality training data to produce accurate results. However, in the V2X slicing controller, training data may be limited, leading to poor model performance.
- •Model Complexity: The V2X slicing controller manages multiple slices with different requirements, such as latency, throughput, and reliability. Designing effective ML/DL models that can handle this complexity can be challenging, requiring networking and ML expertise.
- •The V2X network is highly dynamic, with frequent changes in traffic patterns and network topology. This can make it difficult for ML/DL models to adapt quickly to changing conditions, leading to degraded performance.
- •Security Risks: ML/DL algorithms can be vulnerable to security attacks, where an attacker manipulates the input data to deceive the algorithm. In the V2X slicing controller, this can lead to compromised network performance or security breaches.
- •Interpretability: ML/DL models used in the V2X slicing controller can be challenging to interpret, making it difficult to identify and resolve issues that arise during network slicing, which leads to can limit the effectiveness of the V2X slicing controller in managing network resources efficiently.
Table IV. Review of Various Intelligent Network Slicing controllers in V2X
| Ref./Year | Controller | Method | Focus | Limitations |
|---|---|---|---|---|
| [ | Optimization | Markov model | To illustrate the impact of the considered RRM requirements | High computation |
| [ | Optimization | Graph theory | Reducing the complexity of the slicing construction problem comes from the Markov. | Two steps operation. |
| [ | Optimization | Genetic Algorithm | To minimize the number of unqualified vehicles that have not obtained the required bitrate to meet their desired requirements. | High computation |
| [ | Optimization | Game theory | To increase the eMBB of the dense slices. | High computation |
| [ | ML \ AI | RL | To allow real-time slice elasticity and non-linear reward function. | Increase in latency |
| [ | ML \ AI | DL \ LSTM | To allow the non-linear process to control the dynamics of the system efficiently. | Increase in latency |
| [ | ||||
| [ | ML \ AI | DL \ CNN | To allow real-time slice elasticity. | Complex construction |
| [ | ML \ AI | ML | To meet the inter-slicing requirements in less complexity. | Accuracy concern. Needs big datasets. |
| [ | ML + DL | |||
| [ | ML \ AI | RL | To satisfy inter-slicing requirements in dynamic conditions. | Increase in latency |
This paper will discuss some related work not directly used in V2X to see additional alternatives. Various network slicing architectures, algorithms, and frameworks for 5G networks have been proposed, including those based on reinforcement learning, genetic algorithms, and DL. SDN and NFV in network slicing have also been explored, including using SDR and VNFs to create customized slices for different applications. Additionally, researchers have investigated the use of blockchain technology in network slicing to automate slice management and ensure secure slice access control.
Some of the most recent ML/DL constraints in the V2X slicing controller will be presented:
- •Limited Training Data: ML/DL algorithms require high-quality training data to produce accurate results. However, in the V2X slicing controller, training data may be limited, leading to poor model performance.
- •Model Complexity: The V2X slicing controller manages multiple slices with different requirements, such as latency, throughput, and reliability. Designing effective ML/DL models that can handle this complexity can be challenging, requiring networking and ML expertise.
- •Dynamic Network Conditions: The V2X network is highly dynamic, with frequent changes in traffic patterns and network topology. ML/DL systems must adapt to changes in network performance for accurate predictions.
- •Security Risks: ML/DL algorithms can be vulnerable to security attacks, such as adversarial attacks, where an attacker manipulates the input data to deceive the algorithm. In the V2X slicing controller, this can lead to compromised network performance or security breaches.
- •Interpretability: ML/DL models used in the V2X slicing controller can be challenging to interpret, making it difficult to identify and resolve issues that arise during network slicing. This lack of interpretability can limit the effectiveness of the V2X slicing controller in managing network resources efficiently.
III.CHALLENGES AND SOLUTIONS
Although some of the ML algorithms serve as a potential solution for those optimized V2X networks, there are various challenges associated with their use. Furthermore, intelligent network slicing in V2X networks is an emerging research area that aims to provide customized and efficient network services to support various V2X applications such as safety, traffic efficiency, and infotainment. Nevertheless, there are still some possible solutions available, illustrated in Table V.
Table V. Summary of the open research challenges and their possible solutions
| Challenges | Causes | Possible solutions |
|---|---|---|
| Dynamic environment and conditions of the network. | Use RL algorithms to allow real-time learning of the environment and slice conditions. | |
| Dynamic requirement for each slice. | Simulate different scenarios of V2X slices to gather hundreds of datasets. | |
| Dynamic environment and conditions of the network. Plus, the increasing number of features in each dataset. | Using on-demand training such as using the LSTM algorithm. | |
| Allow edge computing to lower the slice conditions. | ||
| Different requirements of each slice harden the use of standard security algorithms. | Using efficient ML algorithms against attacks. | |
| Individual users may use non-reliance and non-standardized equipment. | Restrict access to the trained dataset. | |
| Frequently changing the certificate of accessing the controller. | ||
| The dynamic and diverse nature of V2X applications and different levels of QoS | Developing efficient SLA negotiation mechanisms and dynamic resource allocation algorithms | |
| Resource allocation | ||
| V2X networks need optimal resource allocation (BW, computing power, and storage) for cost-effective support of varied V2X applications and QoS assurances. | Developing intelligent resource allocation algorithms that can efficiently allocate resources based on the application’s QoS requirements. | |
| Managing interference is a significant challenge in intelligent network slicing in V2X networks | Developing efficient interference management algorithms, beamforming techniques, and resource scheduling algorithms | |
| V2X networks are mobile with fast-moving vehicles, resulting in frequent handovers and mobility challenges. | Developing efficient mobility management protocols and dynamic network reconfiguration mechanisms that can adapt to the changing network topology. |
In summary, many open research challenges exist in intelligent network slicing in V2X networks. Possible solutions include developing efficient algorithms, protocols, and mechanisms to address these challenges and providing customized and efficient network services to support various V2X applications.
IV.OPEN ISSUES AND FUTURE DIRECTIONS
Intelligent network slicing in V2X networks is an emerging research area that aims to provide customized and efficient network services to support various V2X applications such as safety, traffic efficiency, and infotainment. While significant progress has been made in this area, several open issues and future directions still need to be addressed. Also, there is a need to research hybrid machine learning methods dedicated to vehicular communication. The open research issues to be addressed are as follows:
- •Low computation process techniques: The computational load increases significantly with the large datasets produced from V2X networks serving under highly dynamic conditions. This demands the use of high-end processing systems and hardware [60] data conditions. Generally, ML and DL algorithms have been used in network slicing to achieve a variety of objectives, including optimizing resource allocation, predicting network performance, and detecting anomalies. Supervised learning algorithms are commonly used to train models that can predict network performance based on input parameters. Unsupervised learning algorithms can be used to detect anomalies in network traffic or behavior, and reinforcement learning can be used to learn how to allocate resources in a way that maximizes performance while minimizing cost. Overall, ML methods have proven to be a powerful tool for network slicing, allowing network operators to optimize resource allocation, detect anomalies, and predict network performance with greater accuracy and efficiency. Some researchers, such as [25,61], propose hybrid ML methods, on the contrary, that are less process intensive and are specially designed for the taxonomy of vehicular systems. These shall involve a mix of distributed learning and traditional deep nets.
- •Datasets Collection: As also stated in the challenges section, the availability of an all-inclusive dataset is low in V2X due to the dynamic conditions [62]. In such conditions, collecting all the datasets may render a huge size emerging from various network nodes and devices. Therefore, one way is to use a simulative approach for producing a dataset representative of the real environment [63]. Devising data collection mechanisms in V2X is an open research work, with few datasets available.
- •Scenario-based ML Algorithms: It is desired to use hybrid ML algorithms that enable the selection of the most relevant dataset for training purposes [64]. The hybrid models enable generalization using optimization algorithms, including game theory and ML [65]. As a result, scenario-based models have been produced that help reduces the computational load during the training and testing phases.
- •Multi-RAT management and controlling slicing: This is a hot topic in research in the V2X context. The network slicing methods also produce different RAT requirements that should be managed and controlled [66]. Multi-RAT management in V2X slicing is considered an open issue, especially when we look toward autonomous driving, intelligent networks, and ML.
- •Multi-dimensional network slicing: Current research in intelligent network slicing in V2X networks mainly focuses on single-dimensional slicings, such as slicing based on QoS requirements. However, multi-dimensional network slicing is needed to support the diverse and complex requirements of V2X applications, which consider various dimensions such as location, time, and context.
- •Energy-efficient network slicing: V2X networks operate in a resource-constrained environment, and energy efficiency is a critical concern. Developing energy-efficient network slicing mechanisms can reduce energy consumption, improve network efficiency, and prolong the network’s lifetime.
- •Interoperability and standardization: V2X networks involve multiple stakeholders, including vehicles, roadside units, and network operators. Interoperability and standardization are crucial for the efficient operation of V2X networks. Developing standard interfaces and protocols for intelligent network slicing in V2X networks can enable seamless communication and interoperability among stakeholders.
- •ML-based network slicing: ML has shown promising results in various domains, including network slicing. Developing ML-based network slicing mechanisms can provide more accurate and efficient network slicing decisions and improve network performance.
In summary, the open issues and future directions for intelligent network slicing in V2X networks include multi-dimensional network slicing, edge computing in network slicing, energy-efficient network slicing, interoperability and standardization, and ML-based network slicing. Addressing these issues can lead to developing more efficient and customized network services to support various V2X applications.
V.CONCLUSION
The study thoroughly reviewed the network slicing in the V2X networks through intelligent ML algorithms. The work entailed presenting different slicing methods in general, then presenting the limitations and introducing review techniques based on ML. These techniques were further presented in the form of V2X network slicing techniques. Their potential ability to provide lower latency and high throughput has been highlighted. It was further established that data-driven approaches yet limited these intelligent schemes. At the end of this paper, some challenges and open research issues were highlighted. In the future, these techniques can be tested at full potential once the 5G enabling techniques get fully functional and widespread V2X networks can be experienced. In addition, the existing ML algorithms presented in this study shall be analyzed for their merits and demerits across vehicular networks and areas where improvements can be made. The ultimate aim shall be to use hybrid ML and traditional resource-sharing models to make the slicing of V2X networks a reality. In future work, there are several areas where future work could focus on the use of ML/DL for network slicing in V2X. Dynamic slicing, edge computing, improved resource allocation, standardization, and privacy and security are the guarantors of V2X privacy.