I.INTRODUCTION
The interplay between the physical and digital worlds is all that the Internet of Things (IoT) is. Numerous sensors and actuators are used to communicate between the physical and digital worlds. The IoT is described as a paradigm where computing and networking capabilities are built into any imaginable device. These abilities are used to check the object’s status and, if possible, alter it. A three-layer architecture is the most fundamental kind. It was first used in the early phases of this field of study. The perception, network, and application layers are its three tiers. The five-layer architecture also consists of the processing and business levels. Fog computing is a new system architecture involving certain data processing and analytics handled by network gateways and sensors. A layered strategy is presented by fog architecture.
Home automation systems that can help the elderly and those with mobility issues are becoming more commonplace. In such settings, the aged have access to the utmost in both comfort and safety. Patients’ health and happiness are prioritized above all else when it comes to providing healthcare services in the digital realm. However, because of their inherent humanity, the aged will continue to be vulnerable to the kinds of disasters that occur daily. The IoT and other cutting-edge technologies provide us with models and methods that can be used to prevent catastrophic but unforeseen events. In addition, mathematical models can now infer a problem’s gravity with this technology’s help. Before an emergency happens, these models will help field doctors prepare to help seniors and people with special needs. The importance of deep learning in facilitating recent advances in medical care cannot be overstated. Because of this, IoT gadgets can now function in a cordless setting (WBAN). Two examples of machine learning methods that encourage the growth of decision trees and missing value analysis are K-nearest neighbor (KNN) and EM. Both of these things help make the artificial intelligence (AI)-based working components and design more efficient (AI) [1].
The value of an organization’s sensitive data is at risk and subject to significant loss if preventive maintenance is neglected or not performed correctly on schedule. Data loss is unaffordable for businesses because it might include sensitive and important information about their balance sheets or the personal data of their clients. A solid data disaster recovery management strategy is the most effective approach to stopping data loss and dealing with the most recent data breach, malware incursion, or failure of instances. Data backup, in its most basic sense, refers to maintaining multiple duplicate copies of the same data on other devices, hard drives, or locations. A robust encryption system guarantees the security of the data even in the event of theft or an intruder assault.
The smart home is perhaps the IoT application that is now most in demand since it is the most accessible and accessible to customers. There are hundreds of items available on the market that customers can control with their voices to make their lives more linked than ever, from the Amazon Echo to the Nest Thermostat. Watches are becoming used for more than just keeping time. By enabling text messaging, phone calls, and other functions, the Apple Watch and other smartwatches on the market have transformed our wrists into smartphone holsters. By addressing genuine issues that everyday inhabitants confront, the IoT can completely revolutionize whole communities. The IoT may alleviate traffic congestion problems and lower crime, noise, and pollution with the right connections and data. Similar to connecting to a wireless network in a home or workplace, automobiles come with an Internet connection that may be shared with others. Fobs, which have started to replace physical keys in more automobiles, employ sensors to do a variety of tasks, including remote starting, activating the alarm, opening the trunk, and unlocking the car using smart locks.
The age of big data has just been introduced in medical health thanks to the explosive increase of biomedical data and the quick development of computer and medical technologies. Computational medicine started to emerge as a new field in this setting. Computational medicine is an interdisciplinary field that combines medicine, biology, computer science, mathematics, and other sciences. It is based on massive biomedical data and computer technology. By analyzing large amounts of data, it employs AI to deduce human diseases’ fundamentals and physiological underpinnings. This knowledge is used to anticipate diseases, make clinical diagnoses, and deliver medical services. It has been established that deep learning, a subset of machine learning, outperforms classical machine learning in fields, including speech recognition, natural language processing, and computer vision. Deep learning eliminates the need for manual feature extraction, increasing efficiency in both time and resources.
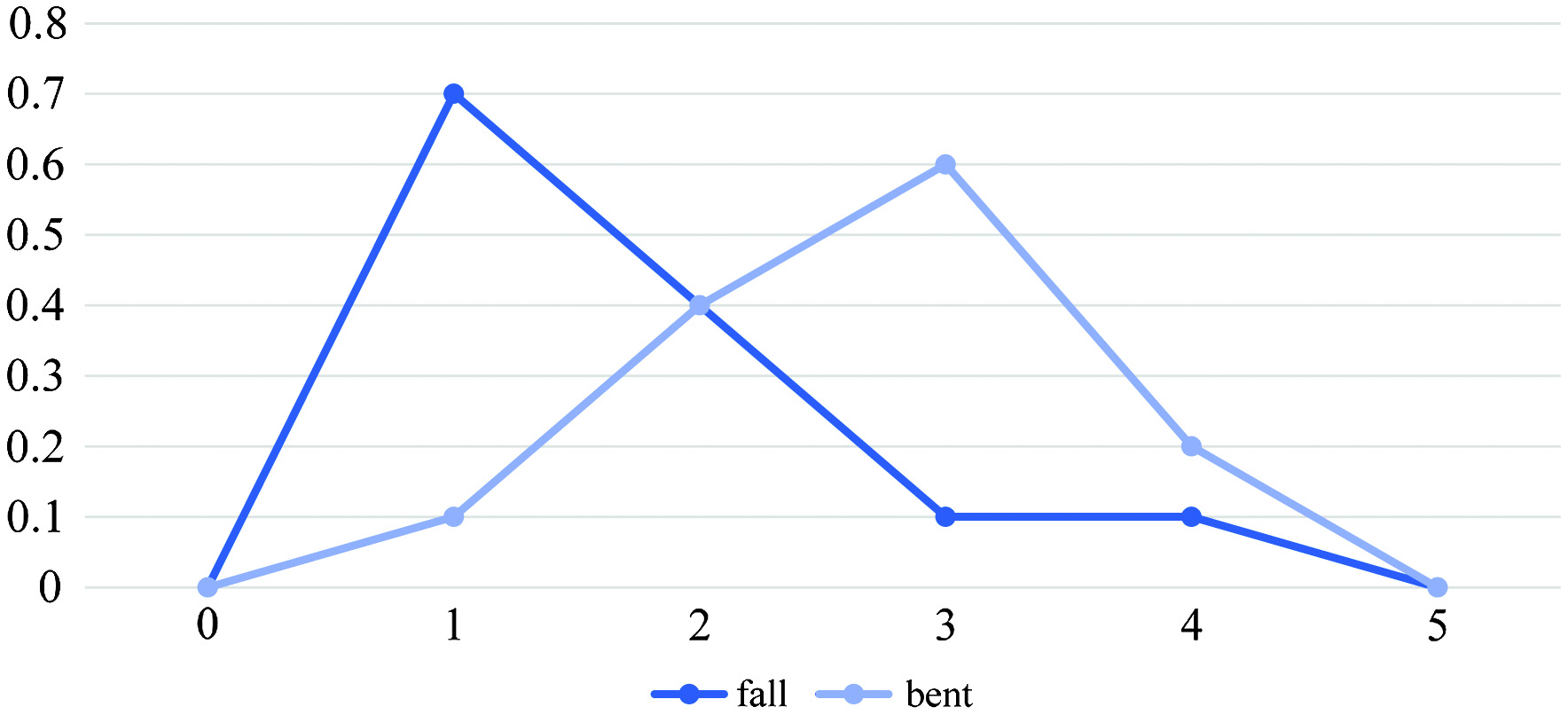
Regression or classification trees are the two decision tree types used in machine learning. Together, these two kinds of algorithms make up the class of “classification and regression trees” (CART), which is occasionally used to refer to them. Their distinct responsibilities are to “classify” and “predict.” Classification trees evaluate whether or not an event occurred. This often has a “yes” or “no” resolution. In the actual world, we frequently make decisions in this manner. On the other hand, regression trees provide predictions about continuous values based on prior information or data. This sort of decision-making focuses on developing algorithms that forecast outcomes based on past trends or behaviors. These researchers wanted to know how often senior citizens living in “smart homes” experience falls or other forms of mobility impairment. Stumbling, on the other hand, was seen as an urgent matter requiring the instant attention of clinical doctors who tended to elderly patients, whereas they regarded bending over as a normal, daily event. The wealth of information now at our fingertips thanks to IoT devices is fertile ground for the creation of an analysis programmer that can both foresee and confirm the repeat of incidents. They propose using the increasingly prevalent barometer sensors among the aged as input for these models. Although using IoT altimeters is nothing new, adding temporal inference models for fall event data has huge implications for the company. A handheld sensor can provide information about the user’s height, which can be used to determine whether an event was a turnover or a fall [1].
Older patients have been described as chatty and fascinating. Several individuals hypothesized that this urge for engagement stemmed from social isolation at home. A few interviewees noted elderly patients’ capacity to engage in a two-way discussion with clinicians despite the cognitive decline, which might hide their cognitive impairment. Communication abilities varied in individuals with cognitive impairment, between patients and within the same patient over time. Communication issues with cognitive impairment offered diagnostic and treatment challenges: Sometimes they are noncommunicative or highly confused or do not tend to respond in entire phrases or answer improperly. Older patients were more likely to report disorientation in addition to physical disease, which meant they might not remember critical clinically relevant events like falls.
IoT analytics is an emerging and challenging area. To analyze, store, and derive commercial value from IoT devices, it ingests enormous amounts of heterogeneous data. For this, various technologies are needed, including data lakes, stream processing frameworks, and analytics tools. Gaining value from massive amounts of data created by devices linked via the IoT is the goal of IoT analytics. Industrial IoT (IIoT) analytics are frequently linked to IoT. IIoT is used by businesses to gather and analyze data from delivery trucks, weather stations, smart meters, manufacturing equipment sensors, pipelines, and other gear. Retail, data center management, and healthcare industries employ IoT analytics.
Because the number of IoT-connected devices may be rapidly expanded in comparison to the number of devices connected to traditional computers, the number of IoT-related attacks has skyrocketed. As assaults, particularly data breaches and identity theft, become more widespread and complex, real-time networked devices must provide enough security and safety in a centralized manner. This becomes painfully obvious when considering ways to safeguard IoT equipment. A deep learning technique was recently published as a unique intrusion-detection system customized to the IoT environment to model and offer proof of scalability and interoperability among multiple IoT-running protocols during network communication.
Any element of a house that includes some level of automation or programmable behavior is referred to as a smart home feature. These features often involve some sort of device or appliance. Additionally, many “smart home” features include a “connectivity” component, either to the outside world or other home components. Senior folks need support and motivation to be involved in their local communities as they age. Evidence about the effects of inaccessible housing for people with mobility impairments on social, emotional, economic, and health outcomes is beginning to emerge. Participants who were socially excluded because of accessibility issues felt dehumanized and isolated, significantly negatively influencing their self-reported mental health. Additionally, the time and effort required to navigate inaccessible housing frequently result in increased degrees of difficulty, tension, and weariness when doing daily tasks at home, such as moving about, taking care of oneself, and providing care for others.
Validation and testing of the suggested time models were performed using both simulated and real-world data obtained from the Internet. Model inputs were derived from processed data derived from actual YouTube recordings of incidents involving slips and bending over. The findings suggest that it is possible to predict and provide a warning of a potential collision. With this information, physicians who have access to the time models can provide the best possible beginning treatment to their elderly patients. The IoT and supplementary processors have emerged as useful tools for smart city apps in recent years, especially those that center on tracking mobile items [2].
Internet Protocol (IP) and Transmission Control Protocol (TCP) are the building blocks of the IoT. The foundation for connecting sensors, devices, and systems to the Internet and to one another is provided by these standards and regulations. Digital-first and physical-first linked devices are the two main categories. The former includes equipment and gadgets that are specially made with connections built in, such as smartphones, streaming media players, mobile payment terminals, agricultural combines, and jet engines. Digital-first devices produce data and use machine-to-machine (M2M) connections to interact with other machines. Contrarily, a microprocessor or a sensor with communication capabilities is part of a physical-first device.
Across heuristic simulations one rule at a time, we decide how the world should function, make sure it makes sense, and then code it in simulations of discrete events. In our world, we create individual actors with specific laws, and then we run those actors to see how the universe changes over time. In simulations based on physics, we use physical principles to examine how a system changes over time [3]. Time series data in particular benefit from the ability to simulate data, which is a field of data science that is rarely taught. This comes as a result of one of the drawbacks of having temporal data: since various events occur at different times, no two data points in the same time series are perfectly comparable. Statistical simulations are the most common way to get simulated time series data. They are especially useful when we understand the underlying dynamics of a stochastic system and wish to estimate a few unknown parameters or evaluate how alternative assumptions affect the parameter estimation process. Deep learning simulations for time series are a new yet interesting area of research. Deep learning has the benefit of capturing exceedingly sophisticated, nonlinear dynamics in time series data even when the practitioner does not completely grasp the dynamics.
This recognition is due in part to the proliferation of “smart city” technologies. However, physical resources like storage and processing power are heavily taxed by deploying IoT and auxiliary computing. All of these factors contribute to the ineffectiveness of generalized monitoring [4]. A subset of the IoT enables online real-time communication between gadgets by linking up machines and physical objects all over the globe in real time, and this facilitates web administration and dealing with a broad variety of tasks. However, people’s lives are at stake if the RT-IoT duties are not finished by the deadline. For this reason, developing a genuine centralized server that can assess, monitor, and track real-time scheduled jobs and various IoT tasks within a smart space from anywhere necessitates designing and implementing a novel architecture in the cloud that is aimed at IoT simulation and formal verification for a typical real-time IoT application [5].
Since attacks, particularly data leaks and identity theft, are becoming more common and complicated, real-time linked devices must provide adequate security and safety in a consolidated fashion. When thinking about how to protect IoT gadgets, this becomes painfully apparent (IoT). To model and provide evidence of scalability and interoperability between various IoT-running protocols upon network communication, a deep learning approach was recently released in the relevant literature as a novel intrusion-detection system tailored to the IoT environment. The above plan of action was conceived as a direct consequence of the study of related materials [6].
The advent of the Internet of Medical Things (IoMT) is frequently cited as the driving force behind IoT’s explosive growth in the healthcare sector (IoMT). The IoMT is a futuristic healthcare infrastructure concept that proposes linking together different types of medical equipment so that they can share and store data for a wide range of uses. “IoMT in Hospital” and “Internet of Medical Things” are two other titles for the IoMT (IoMT). Rapid tracking, accurate diagnostics, pinpointing the source of the problem, and recommending the best course of action are all made possible with the help of machine learning and deep learning algorithms in the medical field [6].
In response to existing multimodal datasets spanning a broad variety of human behaviors, including falls, Martinez-Villasenor, and colleagues developed the UP-Fall Detector Dataset. The authors concluded that a 10-fold design would produce the best outcomes based on prior research and standard machine learning practices. The adaptability of the collection allowed for information to be gathered from numerous sources, including mobile devices, weather monitors, and webcams. They reasoned that experts in human activity categorization and machine learning could use this data to more fairly evaluate the efficacy of different approaches to detecting falls. In addition, this consolidation provides the group in charge of signal identification, vision, and machine learning with fresh opportunities for experimentation [7].
The accelerometer and magnetometer in a smartphone were used to develop a prototype of a gadget that could detect and record falls. If this gadget picks up on something that may portend a disaster, it can notify the appropriate parties. In addition, Tamura et al. developed a portable pillow equipped with a mechanism for detecting falls. Acceleration and angular velocity sensors send impulses to inflate the airbags when the user is struck. A skin-adhesive detecting device was created using a microcontroller, a tri-axial accelerometer, and a Bluetooth low-energy emitter to recognize human falls on its own. After the video is trimmed to eliminate any unnecessary components, the person’s silhouette can be used for fall detection. Using Microsoft Kinect and a two-tiered fall recognition system, they can be confident that they are only counting genuine crashes. To identify a fall, a gadget like this relies on a decision tree [7].
Using an extremely accurate method based on in-house video tracking [8,9], they presume that a person collapsed. In this setting, natural patterns are detected using the Gaussian mixture model (GMM). The detection capabilities of electric near-field imaging for geriatrics are improved by the addition of a floor sensor. Collisions induced by motion can also be detected with delta radar. The aforementioned method alters wavelets to determine if a drop has happened [10].
Machine learning techniques, trained on data from actual occurrences, can detect when an elderly person has collapsed. Some of these systems make use of lumbar monitors, which are worn around the elderly person’s waist to monitor their activity and notify careers of any out-of-the-ordinary patterns. An inference of a fall recognition incident can be made using data from mobile devices in combination with other sources. Further, automatic fall recognition can be achieved by sending data from a wearable biosignal monitoring device to a set of preset reasoning models. Machine learning algorithms utilizing mobile devices can identify movements and forecast crashes. Examples of models in this class include those used for feature selection and classification. Mobile devices can keep an eye on things and sound the alarm before a disaster strike using dynamic threshold models. Low-power, transportable models for dependable pre-fall tracking and forecasts have become viable with the introduction of Bluetooth and the IoT [10].
Two time-based reasoning models (CM-I and CM-II) are utilized in this inquiry to search for instances of possibly fatal falls that had not been considered. Thanks to the growing use of IoT altimeter watches among the elderly, these algorithms may be able to anticipate the risk of a fall based on categorization criteria. To assess the programmers’ work, they contrast real and simulated data containing mistakes, mishaps, and collisions. This study also examines a variety of machine learning and deep learning-based techniques that may be used to identify such breaches because there are numerous IoT systems that are susceptible to cybercriminals’ manipulation. Because the number of IoT-connected devices may be rapidly expanded in comparison to the number of devices connected to traditional computers, the number of IoT-related attacks has skyrocketed. There is no way to solve the problem caused by hacked IoT devices unless they figure out a way to track down the source of the assaults. The ultimate purpose of this research is to get a better knowledge of the technologies, protocols, and design of IoT systems, as well as the potential implications of employing corrupted IoT devices.
II.LITERATURE REVIEW
Machine learning is classified into two types: supervised learning and unsupervised learning. Supervised learning is based on relevant information included in labeled data. Classification is the most common work in supervised learning (and is also the most commonly utilized task in IDS); yet, manually labeling data is costly and time-intensive. As a result, the fundamental barrier to supervised learning is a lack of adequate labeled data. Artificial neural networks (ANNs), support vector machines (SVMs), KNN, naive Bayes, logistic regression (LR), decision trees, clustering, and combined and hybrid approaches are among the conventional machine learning models (shallow models) for IDS. Deep learning models are made up of several deep networks. Deep neural networks (DNNs), convolutional neural networks (CNNs), and recurrent neural networks (RNNs) are examples of supervised learning models, whereas autoencoders, restricted Boltzmann machines (RBMs), and generative adversarial networks (GANs) are examples of unsupervised learning models.
Sharma et al. [10] argue that sensor data, such as air pressure and tri-axial accelerometer measurements, can be used to calculate the likelihood of a mishap occurring in an old person’s smart home. A model with a movable tri-axial accelerometer can identify events instantly because it can monitor movements in all three dimensions. The instant it discovers an error, this gadget can notify the appropriate authorities or personal care workers. Another tool that could be useful in averting disasters in advance is the tri-axial accelerometer. Mendhurwar and Mishra [11] considered that these programmers can predict when an accident will happen, like a stumble, based on past data and current conditions. Using a spectrum analysis model predicated on inertial sensor data and a directed routine, the fall-risk forecast can be calculated. That way, people can be alerted to upcoming autumn events sooner. A directed routine can help one reach their objective. To estimate the pre-impact fall rate of the aged, the fall event recognition technique makes use of two-dimensional data, such as the trunk’s spinning motion and angle.
According to Shah et al. [12] that the frequency with which the elderly experience falls is something that needs to be tracked, so a portable device was designed with a microprocessor, a three-axis gyroscope sensor, a GSM/GPRS interface, and a fall detection algorithm that uses cascade posture recognition. Collectively, they constitute a sophisticated method for detecting accidents. Khanam et al. [13] described that with a low-power fall monitor, they can overcome the problem of wearable technology’s limited battery life by selecting signal characteristics that require less power to operate. There is a model that can tell the difference between unintentional and intentional elderly crashes from great heights, and it can use this information to direct the underlying infrastructure.
Kyriakopoulos et al. [14] argue that this model can be developed and put into action without much in the way of opposition or cost, and it can identify a fall event from the inside with precise precision in real time. A handheld altimeter sensor feeds data into an IoT-enabled model, which then determines whether an incident involving an elderly or handicapped individual in a smart house constitutes a fall or a misstep. Tariq and Sadad [15] described that an identical conclusion was reached in different research that modeled the factors that led to accidents between participants riding a split-belt bicycle to predict and prevent future incidents. This software can adapt to the various speeds at which its users move. The use of freefall libraries allows for the prediction of landings. The records are then used as input for fall probability models, which use supervised feature learning to forecast the likelihood of a fall happening in the future.
The widespread adoption of IoT altimeter watches among the elderly generates a plethora of data that these algorithms may use to estimate the risk of a fall based on categorization criteria. To assess the programmers’ performance, they compared actual and simulated data containing errors, accidents, and crashes. An altimeter is a device that measures the height of an item above a set level [16]. For numerous reasons, an altimeter is the preferred means of navigation when outside. An altimeter can better provide an accurate location because it does not rely on surrounding cell towers or satellites. Because an altimeter relies on barometric pressure, which varies with the weather, users may need to re-calibrate their altimeter while ascending to high elevations. An altimeter will show you the precise height you’re at, which is required for determining air pressure.
Data simulation uses a huge quantity of data to mimic or replicate real-world settings to anticipate future events, choose the best course of action, or test a model. Modeling is the foundation of data simulation. When sufficient computation and memory are enabled, model construction should be simple to complete and quick. Modeling is the foundation of data simulation [17]. When sufficient computation and memory are enabled, model construction should be simple to complete and quick. Multiple imputations are a prominent strategy in medical research for dealing with missing data, but little is known about its application for assessing relative risk. LR and the assumption of multivariate normality are common strategies for imputing partial binary outcomes, although log-binomial models are commonly used to evaluate relative risks. Both multivariate normal imputation and completely conditional specification yielded biased estimates of relative risk, owing to a misspecified imputation model in both cases. Based on simulation results, we propose that researchers employ completely conditional specifications rather than multivariate normal imputation when calculating relative risks and that imputed outcomes be retained in the study.
Shafay et al. [18] studied that numerous researchers have also looked into the possibility of accident forecasts to stop accidents before they happen. Particularly, estimating the elderly’s fall risk by factoring in combinations of risk factors and using data generated by handheld devices is a useful method for verifying fall forecasts. Researchers can examine the differences in gait between stair climbers and strollers by using motion sensors that are worn on the body. Additionally, a conventional standing time model was used to predict falls among the aged [19].
Farooq et al. [20] described that cellphone accessories can help evaluate potential causes of an increased risk of falling. Reasons for this include a lack of strength in the lower extremities, dizziness, and an intense fear of falling. Devices can use this data to predict when an accident might occur. The accelerometer on a smartphone can be used in a similar system to monitor a senior’s movements and pinpoint the position of any potential accidents. Gyamfi and Jurcut [21] argue that the electronic gyroscope and tri-axial accelerometer found in most contemporary smartphones offer one method for predicting the occurrence of accidents. In the event of a catastrophic system breakdown, this plan proposes an escape route based on the user’s current position. Additionally, in some iterations, sensors are employed to discover and predict adjacent hazards to forestall mishaps [22].
A future where data are transferred between physical things like sensors, on-device software, and adjacent technologies with other systems and devices is being created by IoT-connected gadgets [23]. The link between IoT “things” that makes it possible for these exchanges to take place is the key enabling technology. Depending on the needs of the IoT devices involved, different IoT connection types are used. These requirements can range from IoT and interconnected devices that need to communicate occasionally with small amounts of data to always-connected IoT devices that need to communicate large amounts of data at high speeds and with low latency. Tying all of these diverse items together through the Internet of items and equipping them with sensors add a new level of digital intelligence, allowing linked objects to interact in real time and participate in massively automated operations. The number of connections is increasing quickly as IoT grows, and estimates for IoT-linked devices suggest a rising tendency for installations involving several devices connecting to the Internet simultaneously.
Ashraf et al. [24] argue that when researching tip-over events, it is important to look at studies that concentrate on spotting them and anticipating when they’ll happen. They can use sensors and other devices that they carry or put in addition to the sensors and cameras already present in the smart home’s infrastructure. However, determining whether an incident was a fall or a turnover has received little attention in recent years. For improved healthcare in a connected house, the design choice analysis method is suggested. Bibi et al. [25] considered that this system has the potential to increase the security, interoperability, and efficiency of healthcare services through the early identification of exterior events and health threats. To guarantee the quality of its products, architecture tradeoff analysis method (ATAM) conducts in-depth case analyses. In this case, an alert message will be sent and the senior’s family will be notified if data analysis of exterior sensors (gas leakage) or health sensors (falling senior) indicates indications that are not typical for the situation. Ahmad [26] argues that medicine and a warning message will be transmitted to the center along with data in the event of an emergency. By doing so, the senior’s loved ones will be made aware of the issue, which may encourage them to seek assistance. The health information of a person is an example of dynamic data because it is subject to change, while the identifying information, such as their location, is an example of immutable data.
According to Ghosh [27] that if they want to truly understand the challenges faced by the elderly or the handicapped, they need to know the difference between a misstep and an accident. Through the application of temporal inference models, this study contributes to the existing corpus of knowledge in this field by establishing the frequency with which a fall event occurs. Mazhar et al. [28] argue that the proposed models are fed height and time information from a handheld barometric instrument. This information will help them determine whether the incident in issue was a fall or a turnover [29].
IoT offers a variety of inputs for analytical models that may infer and validate fall incidences. Adding temporal inference models for fall incidence verification using IoT altimeter sensors is not a novel strategy. These models’ inputs can use an individual’s altitude data supplied by a wearable sensor, such as the time it takes to descend to the ground, to determine if the occurrence was a fall or a lean over. Sources of anonymous, actual, and synthetic data are mined from the Internet to implement and validate the suggested temporal models. In particular, actual YouTube data for fall and lean-over incident videos is used, which is analyzed to obtain user input data for the suggested models.
III.METHODOLOGY
In this investigation, two time-based reasoning models (CM-I and CM-II) are used to look for episodes of potentially deadly falls that had not been taken into consideration. These algorithms may predict the possibility of a fall based on categorization criteria thanks to the widespread adoption of IoT altimeter watches among the elderly. They compare actual and simulated data involving slip-ups, accidents, and collisions to evaluate the programmers’ performance. They specifically examined 86 randomly chosen YouTube videos, of which 41 depict falls and 45 demonstrate bending-over motions frequently seen in the homes of the elderly and the disabled.
IV.PROPOSED MODEL SETUP
Different laser measuring sensors are used to measure the height of objects that pass below a distance sensor in a range of noncontact applications known as height measurement. In essence, this use is only a different way to measure a distance or a location. A portable sensor’s measurement of the user’s height can be utilized to distinguish between a fall and a turnover in an event. Consider two timestamps, one for the original fall (tF) and another for the following reversal (tB), as an example. The height of an elderly citizen’s adjustable device is h0. If a senior has a mistake, falls, or leans over and h = 0, h = 0, they are considered to have made contact with the ground. Expected values of tF and tB, as well as tA, are normally distributed. That’s because the common definition of “fall” connotes a sluggish, unintentional descent to the earth, while the definition of “tip over” emphasizes the initial acceleration of the fall before it gradually calms down upon impact (PDF). Here, they propose two classification models, CM-I and CM-II, to differentiate between falls and lean overs (bends), Fig. 1 using the normal probability distribution functions (PDFs) of these events as characterized by tests (bend):
With the measures presented here, they will evaluate the efficacy of the CM-I and CM-II classification procedures. This analysis will be performed in the next section. Here is how accurately CM categorization I works:
where sp and sn stand for genuine positive and negative results for CM-I classified events, respectively, and qp and qn stand for spurious positive and negative results, respectively. Learn more about the precise meaning of “classified precision” in the CM-II system here:Accurate positives and negatives in CM-II categories are represented by the characters s′p and s′n, while false positives and false negatives are denoted by the symbols q′p and q′n. The proposed models can be ranked from −1 to 1, with −1 being the worst and +1 being the finest. By comparing the accuracy achieved by the models when applied to the same datasets and assessed utilizing the same criteria, it is possible to determine which classification model is better. Therefore, the performance of a model is measured by how successfully it eliminates or drastically reduces the number of erroneous positives and false negatives. In machine learning, as in other empirical fields, the quality of the training collection does affect the reliability of the forecasts. The discipline relies heavily on perception, which is why this is the case. A more precise normal probability density function is produced when the model is taught with data that is more reflective of the true distribution of the variable of interest (PDF). Multiple factors, including the frequency with which erroneous positives and denials appear, the reliability of the data, and the precision of the forecast, contribute to the overall report quality.
Our group ran special experiments designed to assess the performance of the different classification approaches under review. In particular, they analyzed 86 randomly selected videos from YouTube, 41 of which show a fall and the remaining 45 showing bending-over movements commonly observed in the homes of the elderly and the handicapped. The study results are shown in Table I.
Table I. Experimental parameters
| Parameters | Values |
|---|---|
| Instances of camera recordings of incidents | 87 |
| Fall footage counts | 42 |
| There are a great many movies that feature people bending over | 46 |
| Strategy for evaluating | 10-fold cross-validation |
| Consensus on a Media Industry Standard | NTSC |
| fps: number of frames per second (fps) | 31 |
| Height | 73 |
A.PPG SIGNALS
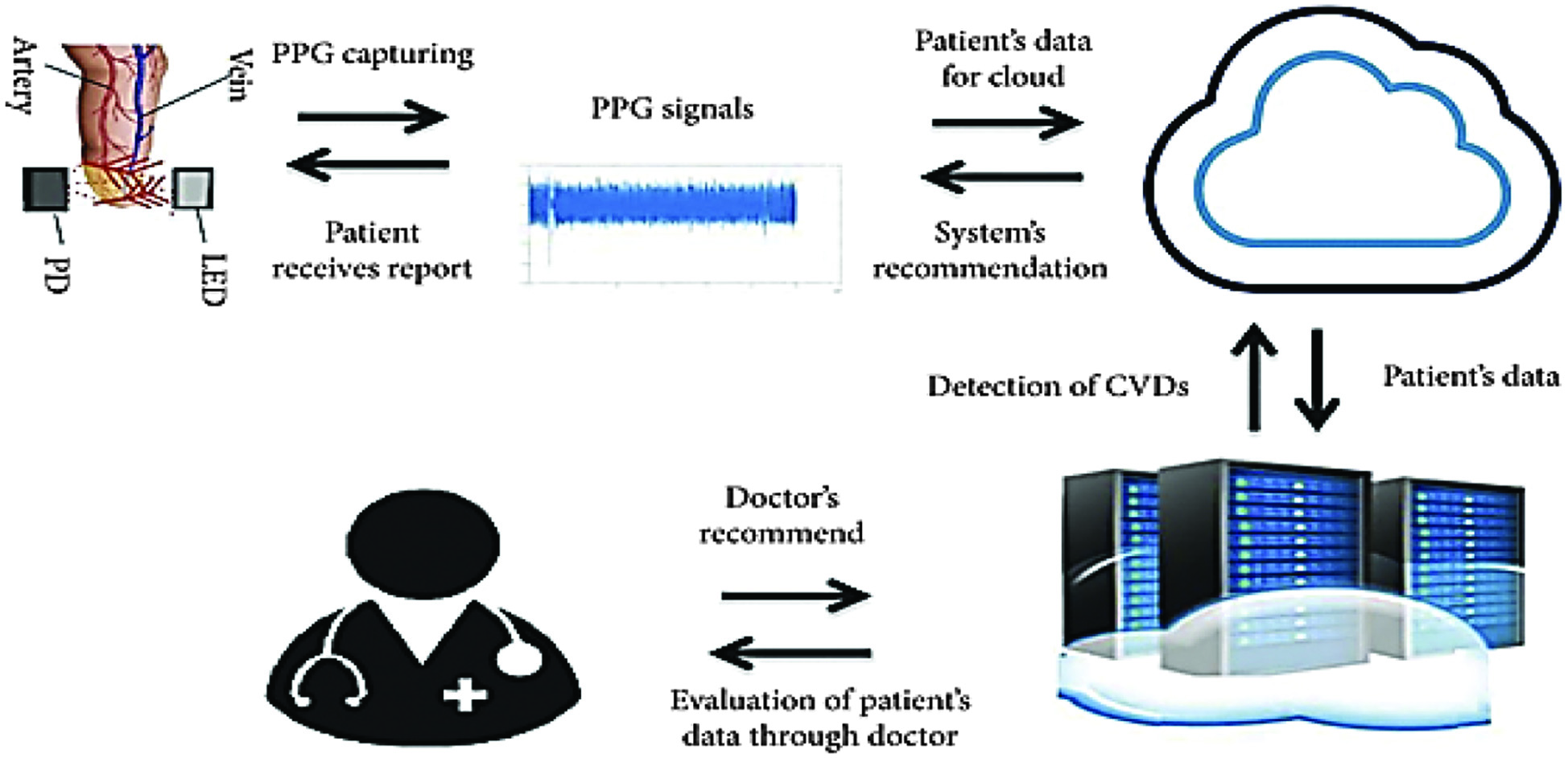
The photoplethysmography (PPG) impulses are processed locally and then transmitted to a distant cloud-based CAD computer. The anxious patient receives a report with the doctor’s prognosis and recommendations for a more effective medicine from the cloud-based machine learning algorithms. The recommended system, which makes use of WPM and a CAD machine housed in the cloud as shown in Fig. 2, has the following overall architecture. People could potentially save both time and money by using such a gadget to monitor their arterial health in comfort.
B.PPG-BP DATASET
The study used information from PPG-BP, a freely accessible database that incorporates PPG and blood pressure (BP). Patients who were transferred to the Guilin People’s Hospital in China are the focus of this archive’s comprehensive medical documents. Everyone’s anonymity is protected at this point. This wealth of information will enable clinical research to investigate the potential associations between PPG indicators and arterial health. Also, the intended rollout of technology must respect users’ right to privacy (e.g., by being small enough to be worn). The vast majority of these measurements are within the Prehypertensive or Normal limits, as shown in Fig. 3. These algorithms may make predictions about the possibility of a fall based on categorization criteria thanks to the widespread adoption of IoT altimeter watches among the elderly. The abundance of data we now have access to as a result of IoT devices makes it possible to develop analytical software that can both predict and validate the repetition of accidents. They suggest that the barometer sensors, which are becoming more common among the elderly, be used as input for these models. Adding temporal inference models for fall event data has significant ramifications for the organization, even though employing IoT altimeters is nothing new. To assess whether an incident was a turnover or a fall, a portable sensor can offer data on the user’s height.
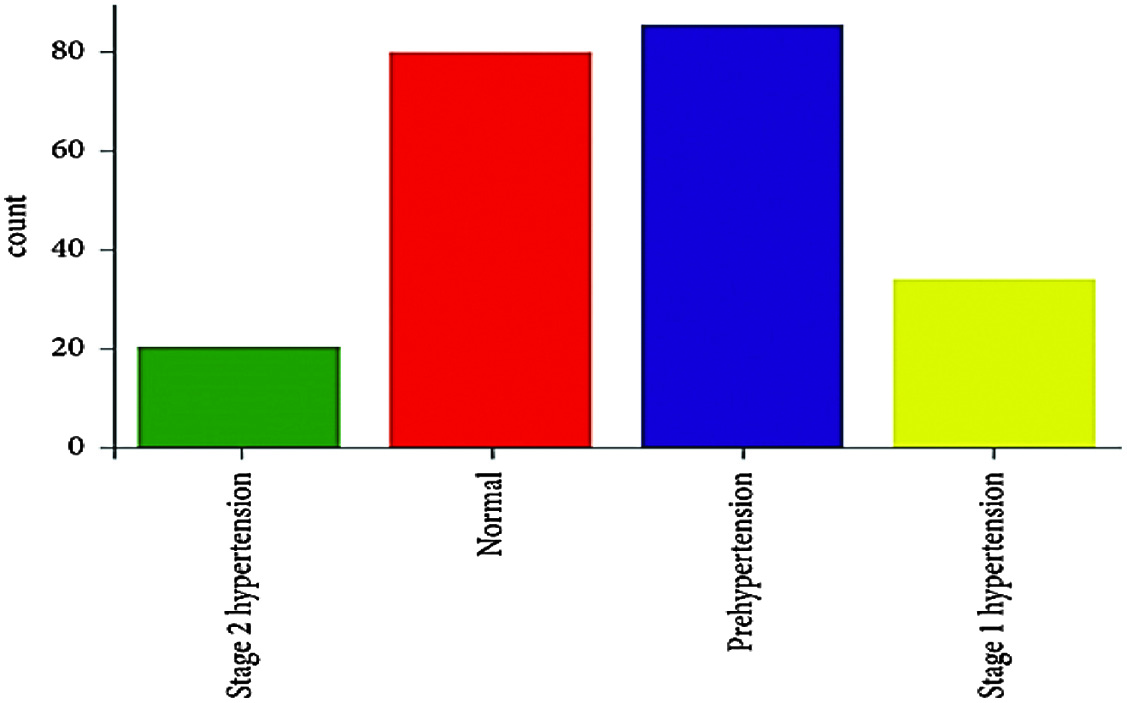 Fig. 3. Distribution of information using pressure.
Fig. 3. Distribution of information using pressure.
The PPG approach, which reflects variations in blood volume with each heartbeat, may be used to detect arterial stiffness noninvasively. The promise of giving a quick biophysical gauge of illnesses or the aging process is perhaps the fascinating use of PPG waveform analysis. PPG estimates coetaneous blood flow by detecting the dynamic attenuation of infrared light by the blood volume present in the tissue. The contour of the PPG in terms of crest time indicated age dependency and clinically important differences between health and illness, including arteriosclerosis, hypertension, and different dermatoses. PPG is mostly composed of arterial pulsations. The oscillating portion of PPG creates a pulsatile wave whose shape may contain information about vascular health. The PPG waveform includes a pulsatile (AC) physiological waveform that is related to fluctuations in the blood volume caused by synchronous cardiac contractions. Since finger PPG is a standard medical method and since it is simpler to record, PPG measurements were performed on the index finger of both the right and left hands.
V.EXPERIMENTAL RESULTS
They used YouTube’s built-in search box to seek for the following keywords to assemble this random selection of videos: They can categorize incidents affecting the elderly and people with impairments into two categories: it both (1) drops and (2) collapses. To complete the study, they utilized a programmer called Power Director, which is designed for video editing. Every video had to be accelerated up to 30 frames per second to comply with the NTSC standard (fps). The character h denoted centimeters as a unit of measurement for height, while the letter t denoted seconds as the unit of measurement for time. Both the CM-I and CM-II algorithms relied heavily on data culled from movies.
To test the reliability of the models, they performed a 10-fold cross-validation. They performed a total of 100 iterations of testing and analysis to minimize random variation. The remaining 10% of the data was used to validate the learned models after 90% had been put to use for training. More specifically, the first 78 events (including 37 falls and 41 lean overs) were used to train the model, and the last 4 falls and 4 lean overs were used to assess the model’s accuracy.
Data are symmetrically distributed and skew-free in a normal distribution. When the data are shown on a graph, they have the shape of a bell, with the majority of numbers congregating in the center and diminishing as they move outward. Due to their structure, bell curves and Gaussian distributions are other names for normal distributions. The same values were used for the mean, median, and mode. Half of the values lie below the mean, and half are above the mean, indicating that the distribution is symmetric about the mean. The standard deviation is a scale parameter, whereas the mean is a location parameter. The peak of the curve’s center is determined by the mean. The curve shifts right when the mean is increased while shifting left when the mean is decreased. The curve is stretched or constricted by the standard deviation. A narrow curve is produced by a small standard deviation, whereas a wide curve is produced by a big standard deviation. You can use a probability density function to fit a normal curve to your data if you know the mean and standard deviation of a normal distribution.
The maximum number of tnI is close to the constant r when h = 0, h = 0. As a result, it seems reasonable to assume that once the incident is over, the value of r will be the same in both instances. Although CM-I recommended doing so once the investigation was complete, CM-II is more efficient because it does so at predetermined intervals.
The experiment’s execution resulted in unique numbers for the assessment measures a and a′. They ran the exercise 100 times to reduce the chance of a fluke result. Please refer to Fig. 3.
In particular, they find that the accuracy of the CM-II categorization model, a′′, converges to the value of 0.98, while the accuracy of the CM-I model, a, converges to the value of 0.62. Both of these figures are significantly more accurate than those predicted by the CM-I model. During the experimental definition portion of CM-I research, the usual PDF of tF and tB is determined once, so this makes logic. With this knowledge, it becomes clear why this is the situation. In contrast to CM-II, which does take into consideration the event’s growing unpredictable backdrop, CM-I does not.
It was decided to compare the suggested CM-II model to other models already in existence in the literature to ascertain its usefulness. When compared to our system, the competition only managed 0.96% precision. The model had an accuracy of 0.95, but the best result that could be obtained using this technique was only 0.92. When compared to the state-of-the-art model presented in, then model presented in is 0.97 times more precise (0.87). Please refer to Fig. 4. When comparing the model’s precision of 0.90 to the strategy’s accuracy of 0.98, the difference is striking. Also, the test was used to determine whether or not the disparity in accuracy between the models was statistically significant. McNemar’s findings show that the suggested algorithms produce highly accurate predictions. Our CM-precision II outperforms all other models in prediction accuracy, and the difference is statistically significant at 0.98. They achieve this by comparing the CM-II model to others that have appeared in the paper (Table II).
Table II. Comparison of categorization models
| Model | Accuracy |
|---|---|
| 1 | 0.96 |
| 2 | 0.95 |
| 3 | 0.92 |
| 4 | 0.87 |
| 5 | 0.97 |
| 6 | 0.98 |
| 7 | 0.90 |
| CM-II | 0.99 |
VI.RESULTS AND DISCUSSION
The healthcare industry needs to make rapid strides if it is to succeed. Digital health is quickly growing as a result of readily accessible medical devices and smartphone applications that provide real-time tracking and treatments. As a result of recent developments in smartphone data transmission and the simplicity and increased reach of getting low-cost electrical components, IoT technology is now commonly used in WPM devices.
When viewed through this lens, advancements in artificial intelligence, automation, and telemedicine are dismissed as inconsequential at best. In 2022, the hospital IoT market is projected to be worth $400.9 billion. The majority of hospitals and clinics now use WMPs, which transmit health information to neighboring smartphone apps and websites. Although these WMP instruments are useful, they are not without their flaws when it comes to precision, accuracy, and dependability. Cardiovascular disease (CVD) is a main cause of mortality worldwide, and hypertension is a significant risk factor for CVD. The research showed that heart disease is the top cause of mortality worldwide. That’s why monitoring your blood pressure is the first line of defense against heart disease (BP). Both passive and intrusive methods can be used to detect hypertension. It is not uncommon for newborns, the newly wounded, and the extremely fat to experience discomfort when using a blood pressure instrument for noninvasive blood pressure measurement. Because there will be such a definitive outcome, the patient may experience anxiety (meaning it must be achieved in a specific number of periods). Taking a blood pressure measurement from a vein to a vein is a highly intrusive process fraught with danger. As in cardiac, constant tracking of vital signs is crucial, making the patient’s house the most advantageous therapy environment. This highlights the importance of a gauge-free, constant blood pressure tracking device.
With PPG, blood pressure can be checked without the use of a strap made of plastic. PPG is a versatile and low-cost device that detects how much light travels through or is returned by a photovoltaic monitor via the capillaries in the skin. Please refer to Fig. 6. Blood pressure is the energy generated by the heart during both the arterial and diastolic stages of its pulse (BP). Using an LED and a screen, it is possible to measure small differences in the amount of light reflected (PD). In addition, PPG provides a highly accurate estimate of BP. Blood flow, heart rate, blood pressure tracking, cardiac output, breathing, arterial aging, capillary control, microvascular blood flow, and parasympathetic function are all cardiovascular factors that can be detected by PPG. Getting a PPG reading is as simple as having a patient wear a monitor on their wrist, finger, or ear. Because of this, PPG is now being considered a viable biosignal for use in portable devices that seek to monitor changes in HR in reaction to exercise. Exertion-related changes in heart rate can be monitored by HR-monitoring wearables.
Researchers measure the efficacy of our classification outcomes with measures like accuracy, confusion matrix, and receiver operating characteristic curve (ROC) curve. Figure 5 displays the obtained precision using the PPG-BP data collection. This statistically verifies that a 99.6% precision was achieved throughout all three tiers of decision trees (fine, medium, and broad). The group classification performed exceptionally well, with an accuracy score of 98%. Please refer to Fig. 7. Decision tree and cluster analysis results can be further evaluated using confusion matrices. Tri-axial accelerometer measurements and air pressure readings from sensors can be used to estimate the chance of an accident happening in an elderly person’s smart home. A model with a mobile tri-axial accelerometer can quickly recognize events by keeping track of motion in all three dimensions. This device may alert the relevant authorities or care providers the moment it detects a mistake. The tri-axial accelerometer is another device that might help anticipate calamities. Based on previous information and the present situation, these coders may anticipate when an event, such as a misstep, will occur. The fall-risk forecast may be computed using a directed routine and a spectrum analysis model based on inertial sensor data. In this manner, people might be informed earlier about planned fall activities. One can accomplish their goal with the use of a directed routine. The fall event identification approach uses two-dimensional data, such as the trunk’s rotating motion and angle, to estimate the pre-impact fall rate of the elderly.
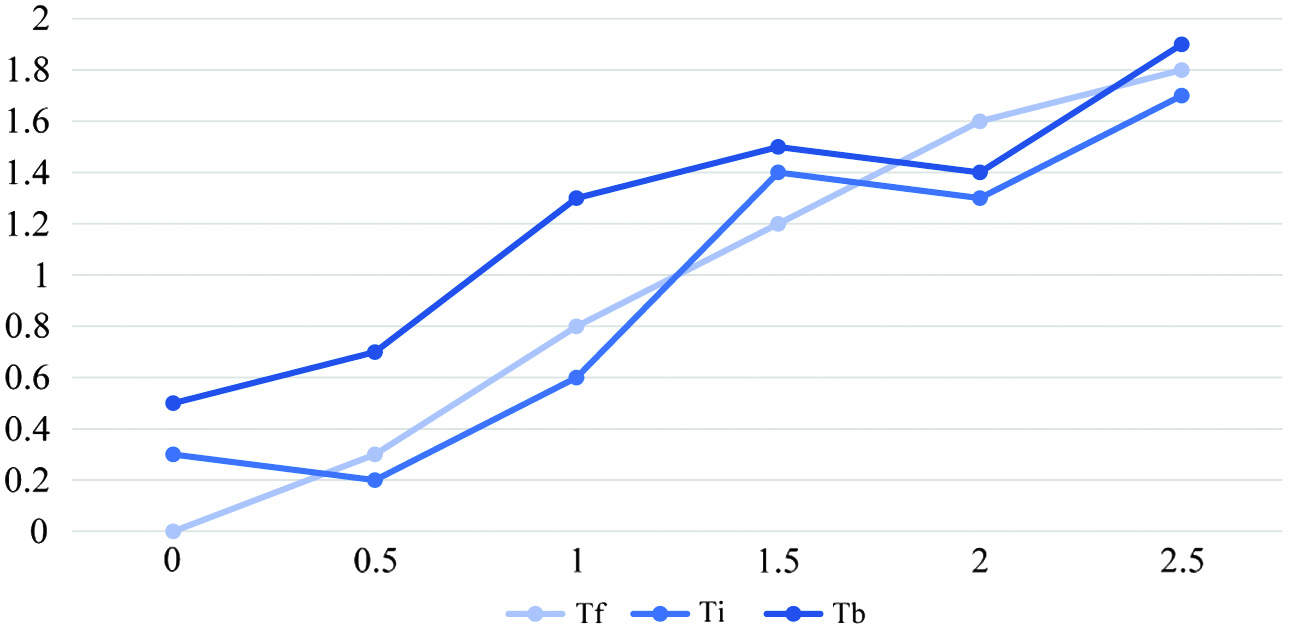 Fig. 4. Time vectors of the categorization models.
Fig. 4. Time vectors of the categorization models.
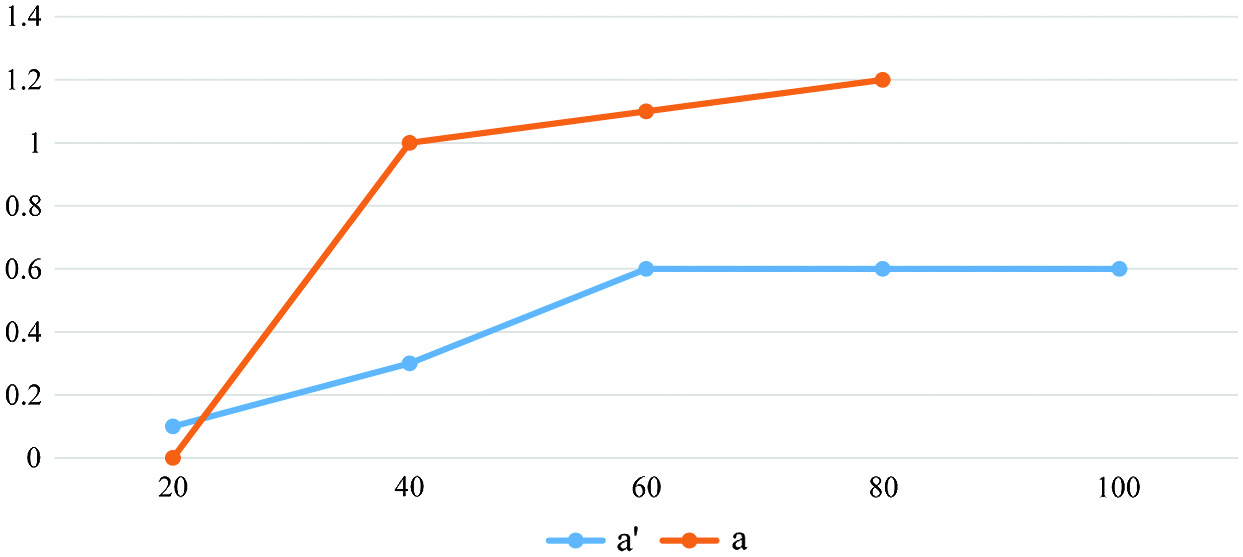 Fig. 5. Accuracy of the categorization models.
Fig. 5. Accuracy of the categorization models.
 Fig. 6. The recorded portion of the PPG signal.
Fig. 6. The recorded portion of the PPG signal.
 Fig. 7. Classification outcomes with measures accuracy, confusion matrix, and ROC curve.
Fig. 7. Classification outcomes with measures accuracy, confusion matrix, and ROC curve.
The clustering algorithm utilized in this study is Clustered Naive Bayes with a Kernel. Because of its simplicity, elegance, interpretability, and resilience, naive Bayes has been widely used in statistics, data mining, machine learning, and pattern recognition research. Even though it is considered a traditional and easy learning approach, it is always efficient and successful. The naive Bayes classifier is the simplest of these models since it assumes that all of the properties of the examples in the class are independent of each other; this is known as the naive Bayes assumption. To deal with nonlinearity and increase classification performance, kernel approaches have recently been coupled with several classification methods.
| Input: |
| Training dataset T, |
| F = (fi, f2, f3,…, fn) // value of the predictor variable in testing dataset. |
| Output: |
| A class of testing dataset. |
| Step: |
| 1. Read the training dataset T; |
| 2. Calculate the mean and standard deviation of the predictor variables in each class; |
| 3. Repeat |
| Calculate the probability of fi using the gauss. Density equation in each class; |
| Until the probability of all predictor variables (fi, f2. f…. fn) has been calculated. |
| 4. Calculate the likelihood for each class; |
| 5. Get the greatest likelihood (Table |
Table III. Accuracy achieved by employing PPG-BP data collection
| Data set | Classifier | Category | Accuracy (%) |
|---|---|---|---|
| – | Tree of deciding | Awesome foliage | 99.6 |
| Medium-sized conifer | 99.7 | ||
| Tree with coarse bark | 90.6 | ||
| – | Ignorant Bayes | Gaussian naive Bayer | 90.5 |
| Clustered Naive Bayes with a Kernel | 87.4 |
VII.CONCLUSION
The study’s goal was to ascertain the frequency with which elderly persons residing in smart homes experienced falls due to tripping or bending over. Some of the data used to train and test the suggested temporal models came from legitimate sources, while other examples were found on the Internet but were later determined to be fake. The CM-II model performed very well at distinguishing between falls and turns because it took into account variables like the duration of the fall and the height of the victim. The study’s findings are encouraging for making inferences and providing prompt notice of the occurrence of a fall, as 99% of falls were placed in the right group. Doctors and carers who work with elderly people in a hospital can make greater use of available data when they have access to time models. There is extensive research being done on the implementation of certain techniques that may enhance existing IoT-based healthcare systems. When compared to training on nonstandardized datasets, the effectiveness of training techniques can be enhanced by using regular datasets. This has the potential to make instruction less complicated and resource-intensive. This is especially clear when considering how heavily they rely on intellect and deep learning. Forgettable qualities can be discussed and illustrated with concrete instances.
VIII.FUTURE SCOPE
Any design must undergo thorough testing and validation before it can be deemed feasible, especially if it has the IoT components. Future efforts to integrate a healthcare system for an aging population with smart neighborhoods and local services will be made easier, since threats that contribute to unfavorable outcomes in terms of qualitative qualities will be easier to recognize. They may proceed now that they have this assurance. A substantial majority of users are happy with the model’s easy functioning, which highlights the model’s adaptability and dependability in terms of user interactions with the IoT, according to study groups and utilization studies employed in comparable research projects. Because of its improved objective, this method is preferred to others for simplifying numerous frequent chores. When modeling falls for safety purposes, academics should keep the distinctions between simulated falls in young, healthy people and genuine falls in the elderly in mind. This means that, despite extensive testing and planning for the project, a model built only from the supplied dataset cannot guarantee an accurate mishap prognosis for old or handicapped people. This demographic may be used as a case study to explore how transfer learning can help seniors and individuals with physical limitations improve their prediction skills.