I.INTRODUCTION
The term “domestic violence” refers to any violent act that occurs between intimate partners who are now living together or who have previously shared living quarters. One definition of domestic violence describes it as “a pattern of coercive tactics of control carried out by actual or threatened physical, sexual, psychological, economic, or verbal abuse, which places an individual with whom there is a past or present intimate relationship in fear” [1–3]. This definition describes an imbalance of power that is maintained by a pattern of coercive tactics of control carried out by actual or threatened physical, sexual, psychological, economic, or verbal abuse [4,5]. People in domestic violence relationships are sometimes sluggish to seek treatment because they do not recognize that they are in a dangerous relationship in the first place [6]. Even though Asian cultural traditions define abuse as a misbehavior, the stigma that praises men and the dread of divorce has stopped women from seeking a remedy and choosing to suffer in silence [7,8]. Domestic violence is classified into seven categories, according to the Domestic Violence Act of 1994, Act 521, including physical assault, psychological and emotional abuse, sexual abuse, detaining the victim, causing property damage, intoxicating the victim, and threatening the victim.
There are currently four significant websites in Malaysia that advocate domestic abuse awareness; one of them is a government-initiative run by the Department of Social Welfare (eJKM Online), while well-known NGOs run the other three websites in Malaysia: Women’s Aid Organisation (WAO), All Women’s Action Society (AWAM), and Women’s Centre for Change (WCC). The eJKM online website, for example, still uses an out-of-date architecture which is 2012. Other websites, such as WAO, AWAM, and WCC, get reports from victims via hotlines, emails, and WhatsApp since they have limitations and lack ways to receive information about domestic violence cases through their websites. One of the limitations is that there is no specific mobile application for domestic violence that provides a Danger Assessment Test (DAT) and navigates victims to nearby shelters for protection after filing a police report. The danger assessment (DA) instrument was developed in 1986 by Jacquelyn C. Campbell, PhD, a well-known researcher at Johns Hopkins University School of Nursing, to aid abuse victims in recognizing when their lives are in danger from an intimate partner. Currently, available websites do not offer a DAT for victims or survivors to better grasp their issues and make the best prediction for them. DA is an integral part of preventing domestic violence. It identifies the level of danger someone is in for them to receive the treatment they require as quickly as possible; as a result, it assists authorities in responding to domestic abuse reports [9].
In Malaysia, a joint effort is being made to turn mosques into domestic violence transit centers with the Federal Territories Islamic Religious Department (JAWI). JAWI’s Director Datuk Mohd Ajib Ismail (2021) claims that 12 mosques have been registered as complaint and counseling centers for domestic violence victims. However, according to the information that we have gathered so far, it is unclear where the public may access the mosque and any welfare centers for victims.
In the past years, mobile applications have started to gain importance in the fight against violence [10]. The significance of utilizing mobile applications in the combat against domestic violence has increased considerably. These applications provide a secure and convenient way for victims of domestic violence to report incidents, as well as access crucial resources and support. Furthermore, these applications have the objective of instructing the general population about the indicators, hazards, and methods to assist individuals impacted by domestic violence.
RELAYVIO is a mobile application that has been specifically developed for the purpose of documenting incidents of domestic violence in Indonesia. The objective of the application is to impart knowledge to the general populace and furnish victims with a forum to document occurrences of domestic violence and disseminate their narratives. In addition, the author with reference [11] developed a mobile-oriented application intended to assist individuals who have experienced domestic violence in lodging their complaints. Both applications employ a software development methodology that enables efficient system development, deployment, and assessment.
The utilization of mobile technology has been employed as a means of preventing domestic violence through the provision of support services to individuals who have been victimized. As exemplified by the study conducted by [12], a mobile-based triage system was implemented to streamline crisis intervention, medication concerns, and the reporting of domestic violence. Additionally, the application functions as a means of alerting individuals in close proximity to provide assistance or act as a potential observer. The system facilitates the identification and correlation of occurrences of abuse, as well as the interconnection with other individuals who have experienced similar mistreatment.
The presumed common aim of these apps is to help victims, bystanders, and/or health workers implement different prevention or response strategies [13]. Hossain et al. [14] developed a mobile application that assists women against domestic violence during a pandemic. The application does not only report their abusive partners but also collects evidences as it will still be accessible online even though the smartphone has been destroyed [15]. Unfortunately, there is no mobile apps available for domestic violence that is developed in Malaysia while most other countries that have developed apps only display basic information of the act, and this raises the questions of how help can be provided and how an emergency call can be made [16,17].
The two goals of this research are (1) to develop an online DAT through mobile applications and (2) to serve as a support system for victims and a platform for Malaysian shelter providers to connect with those who have been victimized. Our DAT module was adopted from Domestic Abuse, Stalking, and Honour Based Violence (DASH) form which consists of 27 questions. DASH had been used widely by United Kingdom Officer since 2009. The application’s feature is receiving reports before victims can go to get help to break out of the abusive relationship. This involves establishing a nearby shelter navigation where victims can seek refuge after filing a police report to demonstrate that empathy still lives. This issue can be solved by employing a mobile application to raise awareness and tell people to find local shelters. The results of this research can be applied practically from the standpoint of both victims and related government agencies to take immediate actions in responding to violence.
II.METHODOLOGY
This study follows the Waterfall Model as the guideline for the methodology framework which consists of four stages: (1) requirement analysis, (2) system design, (3) implementation, and (4) testing.
A.REQUIREMENT ANALYSIS
The purposes and project requirements are decided during this phase. The analysis process comprises of factual information that have meanings in relation to this project. As a result, in this phase, a literature evaluation of related topics from other researchers is completed in order to obtain more useful information. Furthermore, at this stage, a summary of the literature review is completed. Several actions have been carried out in order to obtain the necessary information. The analysis process involves discovering, analyzing, and documenting the information needed.
Additionally, the rise in recorded domestic violence incidents—which prompts victims to contact law enforcement and non-governmental organizations for assistance—is promoting the creation of mobile applications for support systems, which include the DAT and nearby shelter locators. The platform, framework, and programming language that will be utilized to create the Domestic Abuse and Violence Support System (DAVSS) were also selected at this early stage of development.
B.DESIGN
The objective of the design phase is to transform the needs into an exhaustive and thorough system design specification. The successful conclusion of the design phase helps users comprehend the activities and flow that take place in the system. In addition, the design phase can help to fix any systemic issues by the use of (1) case diagram, (2) activity diagram, (3) database design, (4) system architecture, (5) rule based algorithm, and (6) system architecture.
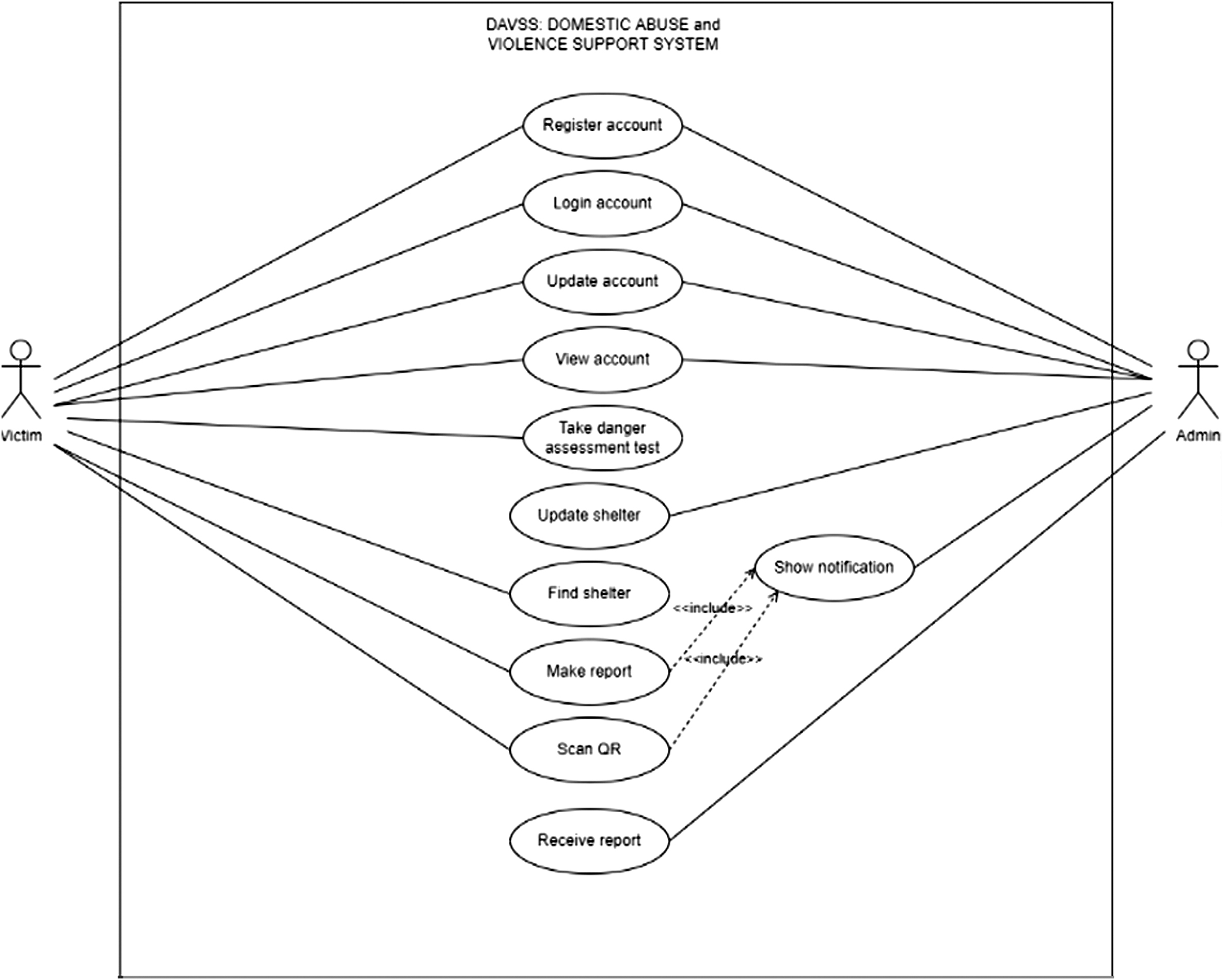
The main functionality of the developed mobile application is depicted in the form of use case diagram (see Fig. 1.). For those who have experienced domestic abuse and violence, this project offers a support system. It has two modules: the victim and shelter provider, both of which might have the same user. The user must first register with the system for the first time before successfully logging in. Users can update their accounts, examine their accounts, perform a DAT, look for a nearby shelter, and report domestic abuse after logging in. Users can scan the QR code once they get to the shelter. As for shelter provider, they can produce QR codes for later usage by shelter occupants, receive new reports, view the current shelter occupant, and amend old shelter information.
In order to use the mobile application, the user must log in to the system by providing their email address and password in the login box. If the user does not have an account, they have to register first. Next, when both inputs for email and password are correct, the user will be directed to the homepage. From there, the user may view the options available including the DAT, making a report, finding shelter, a QR code scanner, and updating personal information. If the user chooses to take the DAT, they must answer all the questions before clicking submit, where the system will display the score and severity result. If the user chooses to file a report, she must first select whether she is applying for herself or on behalf of others, after which she can continue to fill out all the relevant information and submit it once confirmed. Meanwhile, if the user chooses to find a shelter nearby, the user must enter a postal code or a location based on API, and the system will present a list of shelters in the area. If the user opts to use a QR code scanner, she must first decide whether she is leaving or entering and then fill in the relevant fields and begin scanning. The location where the user has successfully checked in/checked out will be displayed. Once the user has completed one of these activities, the system will automatically redirect her to the homepage. As for the shelter provider, the user can edit a newly registered shelter by inserting the address, selecting a location, and submitting the information. A notification will be sent whenever a new report is received, or a new victim enters or exits the shelter.
1)DANGER ASSESSMENT TEST (DAT) RULE-BASED DESIGN
Our approach on DAT aims to assess the potential victims whether they are currently in danger or facing potential domestic violence. All 27 items embedded in DAT as one of important features in DAVSS which are based on the Domestic Abuse, Stalking, and Honour Based Violence (DASH). DASH is a standard risk assessment form that has been used most by United Kingdom police officers to assess victims.
The DASH form, which stands for Domestic Abuse, Stalking, and Honour-based violence, is a uniform risk assessment instrument that is employed by police forces in the United Kingdom. The purpose of this tool is to evaluate the degree of peril that an individual who has experienced domestic violence is exposed to in terms of sustaining severe harm from their perpetrator [18]. The DASH instrument has been specifically developed to facilitate informed decision-making by professionals, with a particular emphasis on prioritizing the safety of both the victim and their offspring. The resource furnishes extensive direction to facilitate the evaluation of the likelihood of domestic violence and proffers recommendations for suitable measures to manage the risk.
Additionally, studies have highlighted the importance of structured violence risk assessment tools within national police forces, such as the Swedish National Police, in evaluating and implementing risk assessment tools for intimate partner violence [19,20]. However, it has been noted that there is inconsistency among British police officers in rating risk, even when using risk assessment tools, indicating potential challenges in the effective use of such tools [21].
Furthermore, in the absence of specific risk assessment tools, police officers have relied on their subjective judgment and experience to assess risk, emphasizing the need for standardized and reliable risk assessment forms such as DASH [22]. The use of risk analysis and risk matrices has also been highlighted in assessing the vulnerability and riskiness of police officers’ work, indicating the importance of structured risk assessment in law enforcement [23].
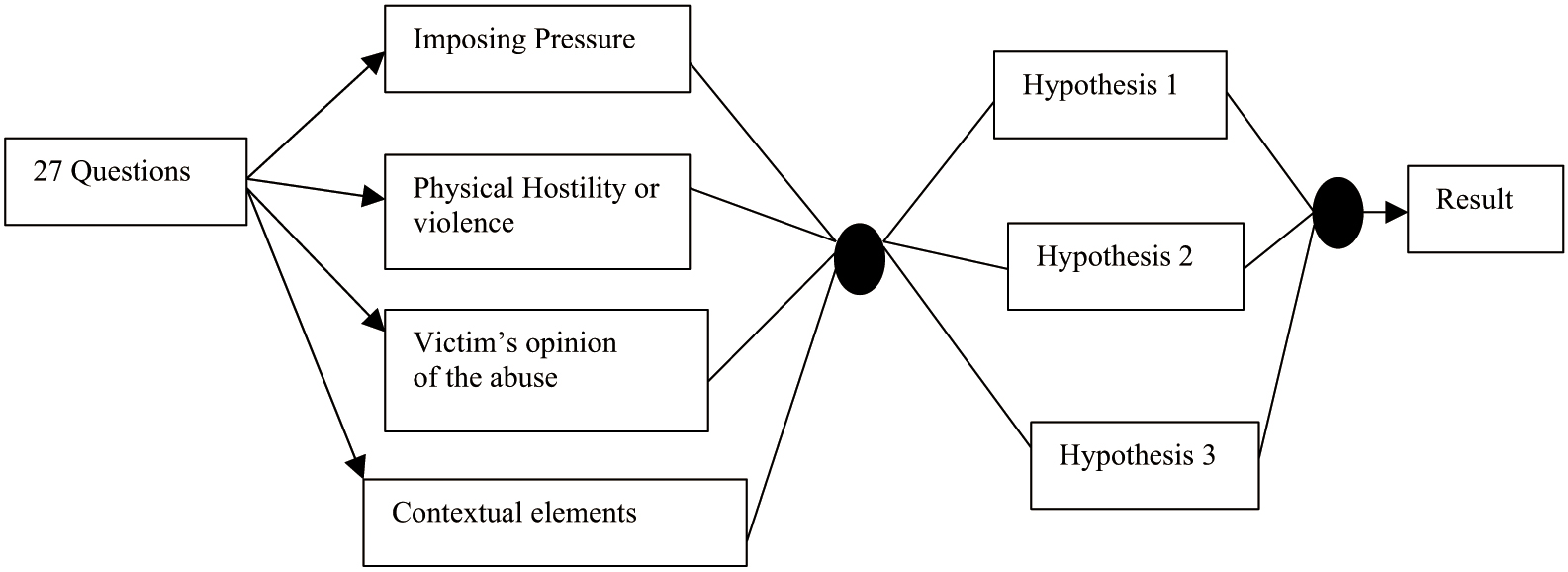
From all 27 DASH assessment question, we develop a rule based to be integrated with our DAVSS application [24,25]. Our analysis on the result of the DAT algorithm is based on the following hypotheses.Hypothesis 1: At some point in the relationship, a pattern of coercive and controlling behavior will be consistent with severe physical acts of violence such as strangulation, choking, and the use of weapons.Hypothesis 2: Domestic abuse that is reported will most often exhibit characteristics of coercive control, such as seclusion, threats, control, sexual coercion, and fear.Hypothesis 3: Isolation, threats, control, sexual coercion, and fear are the characteristics of coercive control that will most often be present in domestic abuse that is reported to the police.
Predictor variables were the responses to DAT questions, which may be “yes,” “no,” or “not known.” The goal of our analysis is to assess the accuracy of the DAT assessments or other methods of scoring based on the DASH questionnaires in terms of future harm prediction. Table I shows the compiled DAT questions which are developed based on DASH.
Table I. Danger Assessment Test questions
| Yes | No | Not known | |
|---|---|---|---|
| Q1. Has the recent event left anyone hurt? | |||
| Q2. Are you really scared? | |||
| Q3. What frightens you? Is there more harm or violence? | |||
| Q4. Do your friends and family make you feel lonely? | |||
| Q5. Are you sad or contemplating suicide? | |||
| Q6. In the past year, did you separate or attempt to separate? | |||
| Q7. Did you believe they were going to kill you or someone else? | |||
| Q8. Is the abuse occurring more frequently? | |||
| Q9. Do they text, phone, contact, stalk, or otherwise bother you all the time? | |||
| Q10. Do you now have a baby or did you just give birth within the last 18 months? | |||
| Q11. Are there any other dependents, such as children or stepchildren who do not belong to the abuser, living in the home? | |||
| Q12. Have they ever harmed the dependents or kids? | |||
| Q13. Have they ever made threats to harm or kill dependents or children? | |||
| Q14. Is there a rise in abuse? | |||
| Q15. Are they overly possessive or overly jealous of everything you do? | |||
| Q16. Has somebody ever wounded you with a weapon or object? | |||
| Q17. Has somebody ever threatened to kill you or someone else, and you took them at their word? | |||
| Q18. Have they ever tried to drown, choke, strangle, or suffocate you? | |||
| Q19. Do they engage in sexual behavior or say or do things that physically harm you or another person? | |||
| Q20. Exists a different person you fear or have been threatened by? | |||
| Q21. Know whether they have injured anyone else? | |||
| Q22. Has the family pet or an animal ever been abused by them? | |||
| Q23. Are there money problems? For instance, have they lately lost their job or are you financially dependent on them? | |||
| Q24. Has the past year seen issues with drugs, alcohol, or mental health that have made it difficult to live a regular life? | |||
| Q25. Have they ever expressed suicidal threat or attempt? | |||
| Q26. Have they ever broken a bond agreement, an injunction, or another arrangement regarding when they can see you or the kids? | |||
| Q27. Do you know whether they have a criminal history or a history of running afoul of the law? |
The questions then populated based on four traits: (1) imposing pressure, (2) physical hostility or violence, (3) victim’s opinion, in their own words, of the abuse, and (4) contextual elements.
- Imposing pressure: This list consists of seven binary items: exclusion from friends and family, complete control over the victim’s actions and excessive jealousy, threats to kill the victim, threats to kill the victim’s dependents, persistent texting, calling, stalking, or harassment, sexual humiliation or abuse, and suicidal threats from the perpetrator.
- Physical hostility or violence: This consists of six binary items: physical injuries in the current incident, previous attempts by the perpetrator to choke, strangle, suffocate, or drown the victim, the perpetrator injuring children, the perpetrator injuring someone else, the use of objects or weapons to inflict harm on the victim, and the perpetrator abusing animals/family pets.
- Victim’s opinion of the abuse: This comprises four binary questions: whether the victim believes the abuse is occurring more frequently, whether the victim believes the abuse is growing worse, whether the victim feels extremely afraid, and whether the victim feels down or is contemplating suicide.
- Contextual elements: This consists of nine binary questions: the presence of children or stepchildren, a recent pregnancy or birth, a dispute over child contact, financial concerns, attempts at separation from the perpetrator in the past or the present, police run-ins, breaches of bail or injunctions, issues with the perpetrator’s use of alcohol or drugs or mental health, and the existence of other people who might threaten the perpetrator.
Figure 2 simplifies the DAT rule-based design. For the 27 questions, the answer is encoded as 1 = yes, risk factor presents and 0 = no/not known, risk factor not present. The answers are then categorized into four traits, respectively, and the results will then be populated based on the hypotheses. The final results then will show whether the victim is in a low, intermediate, or high risk of domestic violence.
C.DEVELOPMENT/IMPLEMENTATION
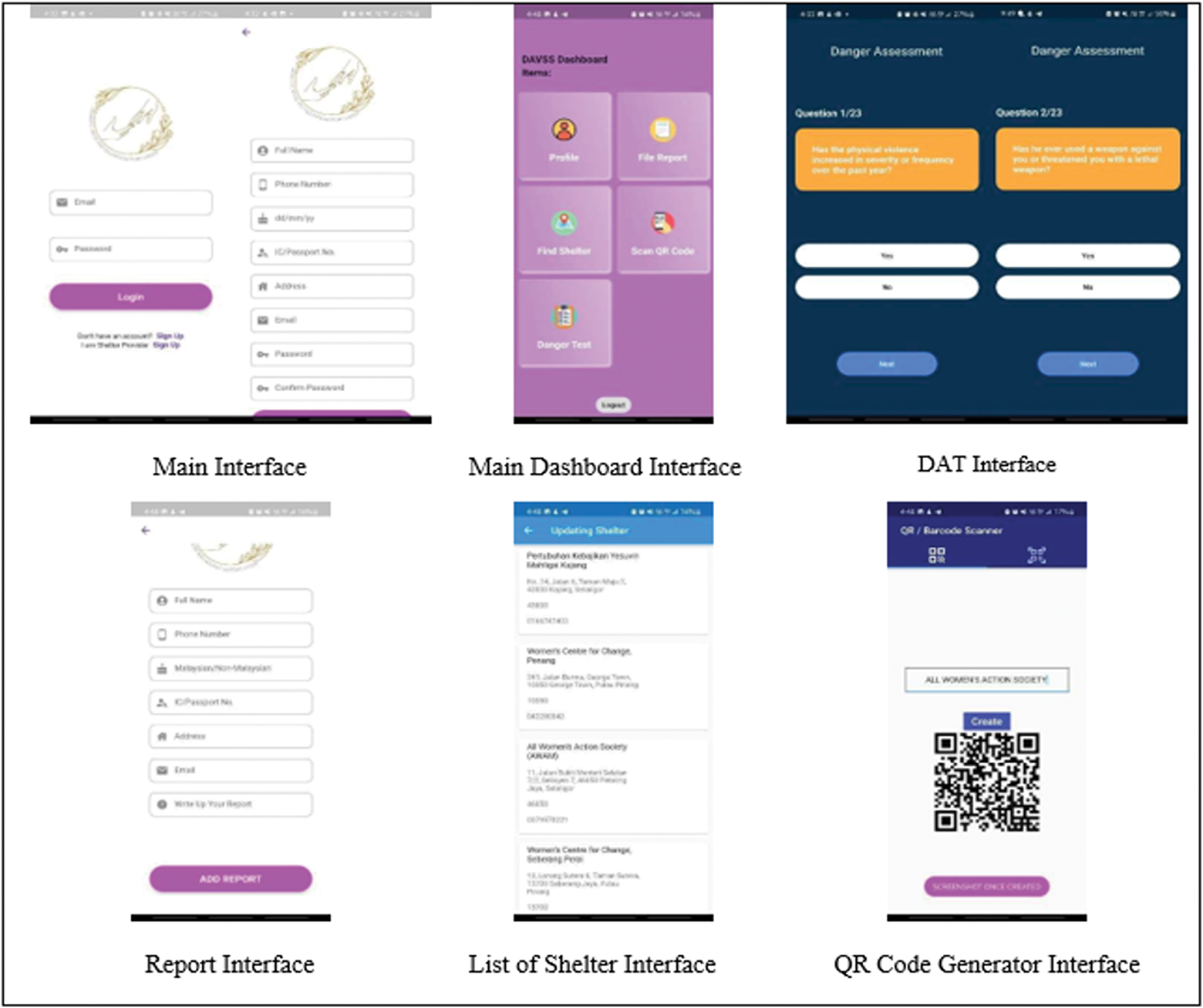
The development of DAVSS was based on eight main modules which conclude the main features of the mobile application. Each module is developed in accordance with the use of the case diagram created during the design phase. Table II depicts the modules involved in the development phase. The example of DAVSS’ interface is presented in Fig. 3. The system under consideration consists of multiple modules that are designed to offer extensive assistance to individuals who have experienced domestic violence. The aforementioned modules encompass a range of functionalities, including Registration, Login, Homepage, User Profile, Make Report, DAT, Find Shelter, and Scanning.
| Module Id | Modules | Descriptions |
|---|---|---|
| 1 | Registration | Users should have an account to use the system |
| 2 | Login | Users should have an account to enter the system |
| 3 | Homepage | Users can view all the facilities provided in the system |
| 4 | User Profile | Users can see and update their profile |
| 5 | Make Report | Users can file a report on domestic violence that includes proof such as images, and it can also be used for personal or on behalf of others. |
| 6 | Danger Assessment Test | Users can take the Danger Assessment Test to determine the severity of their unhealthy marriage. |
| 7 | Find Shelter | Users can look for a shelter nearby for protection. |
| 8 | Scanning module | Users can check in/check out of the shelter |
The Registration component guarantees that users are required to establish an account in order to gain entry to the system. This measure serves to uphold the security and user authentication protocols within the platform. After completing the registration process, users are able to access the Login module and utilize their registered credentials to log in to the system for subsequent use.
The Homepage module functions as the primary focal point of the system. The platform offers a range of facilities and features that are accessible to users. Users are able to traverse various segments in order to locate the assistance they require.
The User Profile module facilitates the ability of users to access and modify their individual profile data. The platform enables users to effectively handle their account particulars, guaranteeing precision and personalization in accordance with their individual preferences.
The Make Report module enables individuals to submit reports regarding incidents of domestic violence. This feature enables users to furnish corroborative proof, such as visual aids, to bolster their arguments. Individuals have the ability to submit reports pertaining to their personal experiences or on behalf of others, thereby establishing a reporting system that is all-encompassing and inclusive.
The module for the DAT offers a mechanism for individuals to assess the gravity of their dysfunctional marital or relational situations. Through the completion of this assessment, individuals can acquire valuable insights regarding the potential level of risk they may encounter, enabling them to make informed decisions regarding the pursuit of assistance or the implementation of suitable measures.
The module entitled “Find Shelter” provides a valuable resource for individuals who require protection. Individuals have the option to conduct a search for shelters in close proximity that offer a secure refuge and critical assistance services. The objective of this module is to facilitate the identification and retrieval of appropriate shelter alternatives for individuals, taking into account their geographic location.
The Scanning module serves to streamline the check-in and check-out procedures for individuals residing in shelters. Through the utilization of this module, personnel responsible for the shelter can effectively oversee and record the current state of occupancy within the facility, thereby promoting optimal administration and safeguarding of the inhabitants.
The modules in question collectively contribute to a system that is comprehensive and centered around the user, with the aim of providing support to victims of domestic violence. The aforementioned features play a crucial role in facilitating reporting, evaluating risk, locating safe havens, and regulating shelter capacity, thereby augmenting the overall support and security afforded to victims of domestic violence.
D.DANGER ASSESSMENT MODULE AND 27-DASH FORM
The Danger Assessment Module plays a pivotal role within the DAVSS application, specifically addressing the reviewer’s comments about the use of the 27-DASH form as depicts in. This module employs the 27-DASH (Danger Assessment for Separation and Harassment) form, a comprehensive questionnaire designed to evaluate the level of danger and risk faced by victims of domestic violence.
The 27-DASH form comprises a series of carefully crafted questions that delve into various aspects of an individual’s experience with domestic violence. These questions cover topics such as threats, access to weapons, patterns of abuse, and the severity of incidents. Each question is designed to elicit vital information from the victim regarding their unique circumstances.
The Danger Assessment Module utilizes a predefined scoring algorithm. This algorithm assigns numerical values to the victim’s responses, taking into account the severity and frequency of indicators of abuse. These values are then aggregated to calculate a danger score, which serves as a critical tool in assessing the level of risk faced by the victim. A higher danger score indicates a more urgent need for intervention and support.
This danger score informs subsequent actions within the DAVSS application, including recommendations for seeking assistance, connecting with shelter providers (as facilitated by the “Find Shelter” module), and reporting incidents (utilizing the “Make Report” module). It empowers victims with valuable insights into the potential risks they face, enabling them to make informed decisions about their safety and well-being.
In summary, the Danger Assessment Module, through the integration of the 27-DASH form and a rule-based scoring system, plays a pivotal role in evaluating the severity of domestic violence situations within the DAVSS application. This assessment empowers users with a clearer understanding of the potential dangers they may encounter, guiding them toward the appropriate resources and support available within the application.
III.RESULTS AND DISCUSSION
In order to verify DAVSS, a usability testing survey was conducted involving 30 participants. The usability of the survey questions is divided into four sections: (1) demographic, (2) system/features, (3) efficiency, and (4) user satisfaction, as shown in Table III.
- 1.Demographic Survey ResultPrevalence of Domestic Violence: A significant finding is that a majority of survey participants had not engaged in domestic violence. This implies that DAVSS has the potential to reach a broad audience, not limited to victims, and can serve as a preventive tool.Perceived Value of the App: More than half of the respondents expressed that a smartphone app is an excellent idea for addressing domestic abuse. This suggests recognition of the potential of technology in combating domestic violence in Malaysia.Awareness of DAT: An interesting observation is that 43.3% of respondents believe the DAT should be taken to assess victimization. This indicates an understanding of the importance of assessing the risk associated with domestic violence situations.Challenges in Finding Shelters: A significant statistic is that 50% of respondents find it challenging to obtain temporary shelters in Malaysia. This underscores the relevance and need for the DAVSS application’s “Find Shelter” feature.
- 2.System/Features Survey ResultsStability and Quality of the Application: The majority of users strongly agreed that the application is stable and well built. This reflects positively on the overall user experience and initial impressions of the application.
- 3.Efficiency Survey ResultsPositive Ratings for Application’s Efficiency: The majority of respondents rated the application with scores of 4 and 5 (agree to strongly agree) across various efficiency aspects. This indicates that the DAVSS application is well functioning, user-friendly, visually appealing, and a promising alternative to traditional methods of addressing domestic violence.Application’s Perceived Value: Users expressing their intention to continue using the app, even if they are neither victims nor shelter providers, is a testament to the perceived value and utility of the DAVSS application. The desire to promote the app to friends and family underscores its importance in raising awareness and potentially preventing domestic violence.
- 4.User satisfactionsPositive Feedback on Functionality: The high percentage (73.3%) of respondents indicating that the application’s various features are functioning as intended is a strong validation of the development efforts. This suggests that the DAVSS application effectively delivers on its intended functions.
Table III. Usability testing survey results
| Frequency (%) strongly disagree–strongly agree | |||||
|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | |
| Have you ever been involved in domestic violence? (As a victim, NGO or to assist/support someone)? | 80 | 0 | 0 | 0 | 20 |
| Do you believe that having a mobile application to assist with handling of domestic violence is a good idea? | 0 | 0 | 10 | 36.7 | 53.3 |
| Do you believe it is a good idea to take Danger Assessment Test to determine whether or not you are a victim of domestic abuse? | 0 | 0 | 16.7 | 40 | 43.3 |
| Do you consider that if you are a victim of domestic abuse, it is difficult to find temporary shelter in Malaysia? | 0 | 0 | 6.7 | 43.3 | 50 |
| Do you know of any government or non-profit organizations that are attempting to combat domestic violence in Malaysia? | 0 | 0 | 16.7 | 43.3 | 40 |
| This application is stable and well constructed. | 0 | 0 | 16.7 | 66.7 | 16,7 |
| Each functionality of the application works properly. | 0 | 0 | 10 | 73.3 | 16.7 |
| The application allows me to do a Danger Assessment Test and display the results. | 0 | 0 | 6.7 | 73.3 | 20 |
| The application let me find related shelters in Malaysia. | 0 | 0 | 6.7 | 73.3 | 20 |
| The QR code generator and scanner are working properly. | 0 | 0 | 33.3 | 50 | 16.7 |
| The DAVSS application looks appealing. | 0 | 0 | 0 | 23.3 | 76.7 |
| I like the application’s interfaces (simple to handle). | 0 | 0 | 0 | 36.7 | 63.3 |
| The application is well organized. | 0 | 0 | 0 | 40 | 60 |
| DAVSS application is beneficial in combating domestic abuse in Malaysia | 0 | 0 | 3.3 | 40 | 56.7 |
| Satisfied with the application overall. | 0 | 0 | 10 | 60 | 30 |
| I will recommend this application to other people and close friends. | 0 | 0 | 6.7 | 60 | 33.3 |
| I will keep on using this application even when I’m not in danger. | 0 | 0 | 10 | 56.7 | 33.3 |
Efficient Feature Usage: The feedback regarding users’ ability to quickly scan QR codes, discover shelters across Malaysia, and take the DAT further supports the application’s effectiveness. These features align with the goals of providing support, information, and assessment tools to users in domestic violence situations.
The results of the usability testing survey provide substantial evidence of the DAVSS application’s effectiveness, perceived value, and positive user experience. It appears to be a well-received tool that not only serves victims but also has the potential to raise awareness and facilitate preventive efforts against domestic violence in Malaysia. The findings validate the achievement of several project goals, particularly in terms of functionality and usability.
IV.CONCLUSION
In conclusion, the DAVSS application represents a significant step toward addressing the critical issue of domestic violence in Malaysia. Our research has been primarily dedicated to the development and evaluation of this mobile application, which integrates the vital DASH-27 questionnaire to assess the gravity of domestic violence situations.
The DAVSS application, developed through a structured approach encompassing the Waterfall Model’s phases, offers a multifaceted solution. It not only enables victims to report incidents promptly but also assists them in finding refuge to receive protection. A distinctive feature of the application is its innovative use of QR code scanners for shelter entry and exit, enhancing user safety and convenience.
Our usability testing results have shown that users are generally satisfied with the application. However, we acknowledge that the usability testing’s reliance on frequency alone can be enhanced by incorporating other measurement methods such as median and standard deviation approaches. This will further refine and improve the reliability of the system.
Additionally, it is important to note that our DAT rule-based algorithm, based on the 27-DASH questions, is a significant component of the application. In our future work, we recognize the need to validate this algorithm by engaging experts using techniques like the Delphi method. This validation process will add a layer of expertise and credibility to our DA approach.
Given that Malaysia lacks dedicated mobile applications to aid victims of domestic abuse, the DAVSS application holds immense potential. It not only offers practical assistance to victims but also serves as a crucial platform to overcome obstacles hindering victims’ voices from being heard. As domestic violence continues to demand more attention and support, DAVSS stands as a valuable system that extends its hand to the victims, providing them with the help and resources they need in their journey toward safety and recovery.