I.INTRODUCTION
The Internet of Things (IoT) is expanding rapidly, reaching several domains including personal health care, environmental monitoring, home automation, smart mobility, and Industry 4.0 [1,2]. The report of Industry Revolution 4.0 by Juniper Research predicted that the total number of Industrial IoT sensors in use will increase from 17·7 billion in 2020 to 36·8 billion in 2025, representing an overall growth rate of 107% [3]. Wireless sensor networks (WSNs) are a core technology that can provide a large volume of heterogeneous data from the long-term observation of large-scale scenarios [4]. The main objective of sensor networks is to sense the environment and send information to a base station for further communication and processing [5].
The main challenges associated with WSNs are network security, load balancing, and network life cycle. WSNs are usually deployed in unsupervised and insecure environments, and their nodes can be attacked and destroyed by malicious attackers. Attackers can also use compromised sensor nodes to disrupt communications or insert misleading sensor data. Furthermore, sensors are generally powered by energy-constrained batteries and have limited computational ability. These challenges must be considered and addressed while designing WSN protocols. Therefore, it is vital to detect faults and enhance the overall performance of the network by monitoring network activities, minimizing risk, and ensuring that network activities, such as data gathering and data processing, can be performed without interruption.
Several studies and surveys have been conducted [6–10] to address the security concerns associated with WSNs. However, existing security methods are limited to a certain stage of transmission and balancing the trade-off between improving the transmission performance of WSNs and data security. In this study, we improve a data transmission method based on ant colony optimization (ACO) and threshold proxy re-encryption to defend against internal and external attacks from the data path selection phase and the data encryption phase, which method can find a suitable trade-off way between security and network performance. The path selection phase approach in the ACOTPRE is based on ACO and can determine an optimal route from source to destination through the continuous accumulation and updating of pheromones. Data security is achieved by a proxy re-encryption-based threshold algorithm that uses intermediate nodes to protect data from malicious attackers. In addition, we also compare the simulation results of ACOTPRE with those of AODV (Ad hoc On-Demand Distance Vector Routing) and ReTE-AODV (refined trust energy ad hoc on demand distance vector routing algorithm) [11]. The main contributions of this study are
- •Aiming at internal attackers, this paper improves a data path selection scheme based on ACO. This paper proposes to reconstruct the pheromone concentration factor, including trust evaluation model, residual energy model, and node signal strength. When selecting the next hop node, it fully considers the impact of internal attacks, network energy consumption, and transmission link quality. It is proposed to improve the pheromone update strategy, considering the average and minimum node energy. Compared with the traditional ant colony algorithm, the improved scheme fully considers the characteristics and requirements of WSNs.
- •Aiming at external attackers, this paper improves a data encryption scheme based on proxy re-encryption. The source node uses Lagrangian interpolation polynomials to construct the re-encryption key fragments and distribute them to the proxy node. The destination node calculates the Lagrange interpolation polynomial recovers the symmetric key. According to the threat model proposed by the characteristics of WSNs, the corresponding security analysis is carried out.
- •The simulation experiment compares the ReTE-AODV and AODV protocols and evaluates the performance of packet delivery ratio (PDR), end-to-end delay (EED), and average residual energy (ARE). The simulation results show that the ACOTPRE scheme sacrifices some transmission time and energy consumption to ensure secure data transmission, but PDR is increased by 19% and 22%, respectively.
The rest of this paper is organized as follows: in Section II, we present a brief review of related work; in Section III, we describe ACOTPRE architecture, first presenting the routing protocol and then explaining the use of proxy re-encryption in WSNs; in Section IV, we perform simulation experiments to evaluate the performance of the proposed approach and discuss the results of the experiments; finally, we conclude the paper in Section V.
II.RELATED WORK
This section investigates and analyzes existing methods for enhancing security in WSN environments. Some of these methods aim to enhance the security of the routing phase, whereas others focus on data security.
A.ROUTING PROTOCOL IN WSN
Due to the open medium and dynamic entry of new nodes in WSNs, routing protocols must establish trust relationships to avoid malicious nodes [12]. Pirzada et al. [13] proposed a trust-based routing protocol, wherein trust agents obtain trust levels from events that are directly experienced by the nodes. The trust values of all subsequent hops in the path are compared and the hop with the highest trust value is selected. The trust–distrust protocol (TDP) [14] is divided into four phases. The fitness calculated in the second phase of the link quality assessment is used as the trust parameter in the third phase. In the fourth stage, path selection is performed based on the ranking of the trust capabilities of the nodes. The energy of sensor nodes is limited and must be considered while designing routing protocols. A novel Metric-based RPL (Routing Protocol for Low-power and Lossy Networks) Trustworthiness Scheme (MRTS) was proposed in ref. [15], combining selfishness, honesty, ETX, and four energy parameters to evaluate the credibility of a node. The MRTS can be adjusted by adding or deleting behavior combinations for specific IoT applications. The self-channel observation trust and reputation system (SCOTRES) [12] is another novel trust management scheme that integrates with the DSR (Dynamic Source Routing). It is assessed by direct and indirect knowledge and includes four metrics in the direct assessment. However, it differs from previous schemes as it includes channel health metrics, which provide tolerance for periodic failures due to bad channel conditions and protects the network from jamming attacks. ReTE-AODV was introduced in ref. [11] using Bayesian probability for trust management, owing to its ability to handle uncertainty while obtaining a refined form of the trust calculation, allowing it to select a reliable route that consumes low energy and sends packets in a trustworthy manner.
Cryptography can also be used in WSNs. A secure routing algorithm based on energy optimization (EOSR) [16] can improve the security of a route by distributing a public–private key pair before deployment. The secure identity-based routing protocol [17] introduces node identity authentication to ensure the security of network routing and prevent witch attacks and wormhole attacks. The elliptical curve encryption algorithm is used for the route discovery process to ensure that the nodes discovered are credible. This protocol also uses an energy threshold to ensure that the nodes do not consume excessive energy. Sreevidya et al. [18] proposed the use of an ACO algorithm to identify the formation of cluster nodes in mobile sensor networks, designate cluster head nodes, and establish routes using the AODVRP routing protocol and the Diffie-Hellman Key exchange (DHKE) algorithm to achieve safe data transmission and reduce the number of nodes and the overhead of storing public keys.
B.PROXY RE-ENCRYPTION
The concept of proxy re-encryption was first proposed by Blaze et al. in 1998 [19]. Subsequently, Ateneses et al. [20] proposed the first one-way proxy re-encryption scheme. The proxy was given a re-encryption key that could convert Alice’s ciphertext to Bob’s ciphertext without understanding the message encrypted under any key. Currently, proxy re-encryption is widely used as a tool in encrypted data storage and data sharing to protect the confidentiality of data stored with third parties, such as electronic health records, cloud computing, and digital rights management. Due to its relevancy, it has been utilized in identity-based PRE schemes [21,22], wherein the user’s public key is regarded as their identity. However, the scheme proposed in ref. [22] still faces the threat of collusion. Consequently, a one-way threshold proxy re-encryption scheme was applied to the blockchain in ref. [23], which solved the problem wherein the use of a centralized CA for identity verification can result in hidden safety hazards when a new node starts to communicate with nodes in the blockchain network.
The SHIB-PRE scheme [24] proposed a new concept for WSNs of proxy re-encryption of the source hidden identity, which supports the gateway in the wireless network to directly transfer the encrypted data of one user to another. The underlying plaintext data is disclosed throughout the sharing stage, but the agent must be a gateway or cloud.
The scheme proposed in ref. [25] is a conditional proxy broadcast re-encryption scheme that supports regular release but does not provide flexible encryption and complete security certification. A time and ID-based agent re-encryption scheme was proposed in ref. [26] that does not require any trust in the agent but adds a time element so that the sender can further divide the message into fine molecules based on the specified time period to provide agents with more fine-grained re-encryption capabilities. The timed-release proxy conditional re-encryption scheme [27] is a more flexible encryption method. In addition to ensuring the privacy of user files under the constraints of time factors, each user can freely communicate with another user to share files. The recipient does not obtain any information regarding the file until the specified time.
Reference [28] presented a data security re-encryption scheme based on the trusted authorization that takes advantage of the performance required for re-encryption tasks within the cloud. Trusted authorities are only responsible for key regeneration, thereby achieving efficient and scalable security. In the VANET (vehicular ad hoc network) scenario, Kanchan et al. [29] presented a technique which group signatures are combined with non-transit proxy re-encryption technology to enhance the security and effectiveness of messages sent over the network without requiring multiple re-transmissions. This algorithm uses the bilinear Diffie–Hellman method, which cannot be easily broken by opponents. It can manage keys and decryption rights using agents and PKG, respectively, thereby reducing the workload of the member manager. A multi-agent proxy re-encryption scheme [30] was constructed using proxy re-encryption and re-splittable threshold passwords in the grid, but each ciphertext fragment in the scheme requires verification, which would inevitably lead to significant computational overheads and reduce the scalability of the system.
The above analysis demonstrates that insecurity can be easily introduced into the network due to the characteristics of the WSN, and that existing security methods are limited to achieving a balance between improving the transmission performance of the WSN and data security. The method proposed herein performs these tasks in coordination, thereby improving the overall performance. ACOTPRE is a WSN data transmission method based on ACO and proxy re-encryption, including the data path selection phase and data encryption transmission phase. A reliable routing protocol is required to provide complete security during both these phases. For the path selection method based on the ACO algorithm, the optimal path for data transmission from the source to the destination can be determined through the continuous accumulation and updating of pheromones. Data security is realized by using a proxy re-encryption algorithm for the intermediate node to prevent malicious attackers from accessing the data, thereby enabling the safe sharing of the final data.
III.ACOTPRE ARCHITECTURE
This section presents a framework of ACO and proxy re-encryption algorithms to improve WSNs considering two common problems—optimal path selection and reliable data transmission.
A.DATA PATH SELECTION PHASE
1)SYSTEM MODEL AND ASSUMPTIONS
The network monitoring area is assumed to be a circle. A total of N sensor nodes are randomly distributed inside the circle and the base station is located at the apex of the network monitoring area. In addition, making the following assumptions: 1) once deployed in the network, sensor nodes do not move coordinates and correspond to a unique coordinate position and ID identification. 2) Each node in the network acts as both the source node and the forwarding node, and the base station only serves as the destination node. 3) The base station has enough energy, and the other node has the same initial energy. The topology of this WSN is shown in Fig. 1.
2)ROUTING ALGORITHM DESIGN
The problem of secure routing in WSNs is a combinatorial optimization problem, wherein the data of each node can be transmitted to other nodes more reasonably. The ACO algorithm is a metaheuristic algorithm for combinatorial optimization problems and can be used to solve complex dynamic combinatorial optimization problems to improve network security and prolong the life cycle of the network. To design a safe and efficient routing algorithm, we introduce the node trust model, energy consumption, and signal strength of the node into the ant colony algorithm, as pheromone concentration factors. At a time t, each ant selects a path for the proposed improvement of the ACO algorithm, as indicated by the probabilistic formula:
The influence of the pheromone concentration H and the distance on message propagation are simultaneously considered during routing, and H(t) represents the pheromone at the time t. The heuristic function , denotes the distance between the source node i and the intermediate node k, and represents the distance between the intermediate node k and the destination node . The impact factors α and β control the influence of the pheromone intensity and heuristic information, respectively.
C)CALCULATION OF PHEROMONE
The first pheromone factor is a node trust model, which includes the direct trust and the indirect trust, to detect the interaction behavior of each node. The trust degree of a node is an indicator of the security of the node and remains in the interval [0,1]. Normal nodes can easily participate in excessive route discovery while implementing security measures, thereby consuming the available energy in a short period of time, exiting the network prematurely, and affecting the quality of communication. Therefore, we propose calculations for the energy percentage and link quality to improve the stability of data transmission.
Trust Model: A trust model essentially performs trust derivation, computation, and application [13]. Trust evaluation in a routing procedure is an assessment of the forwarding behavior of neighbors by a sender. In this study, we analyze the behavior of receiving and forwarding packets and the characteristics of the monitoring capability of neighbor nodes considering the following: 1) packet contents may be too large; 2) the number of packets is too large, which may result in a denial of service attack; and 3) the node does not forward packets or modify content forwarding. Two indexes, namely, the packet content repetition rate and the packet number, are chosen as evaluation parameters. The direct and indirect trusts of the node are determined by adopting an appropriate trust model and weighting each trust to obtain a comprehensive trust value for each node. The comprehensive trust value is introduced into the ant colony algorithm as one of the pheromone concentration factors.
As stated, the indicators are determined considering two aspects—packet content repetition rate and the number of packets [31]. The direct trust can be defined as a vector :
where Rij(t) is the packet content repetition rate and Nij(t) is the number of data packets. The specific measurement formula iswhere nij(t) is the number of data packet transmissions at a time t, rnij(t) is the number of data packet transmission repetitions, and Δnij(t) is the expected value of data packet transmissions. These factors have different proportions for different application requirements, and the weighted average method can be used to calculate the direct trust of node i and node j. Here, the weight is represented by the vector W: where 0 < wR, wN < 1 and wR + wN = 1. Therefore, the direct trust of the actual node is . Once the network node is initialized, the initial direct trust as node i and node j do not interact. The node update cycle is Δt. Once the update cycle is reached, the node responds to dynamic changes in real time and updates the direct trust.Indirect trust is calculated by the feedback evaluation value provided by the neighbor node, and it cannot recommend the received recommendation information from one node to another. The indirect trust may incur additional communication costs for trust exchange. To simplify the trust model, only the history of direct interactions between nodes is used to compute trust. In this way, the iteration of trust value transmission can be avoided. The direct and indirect trust between nodes is shown in Fig. 2.
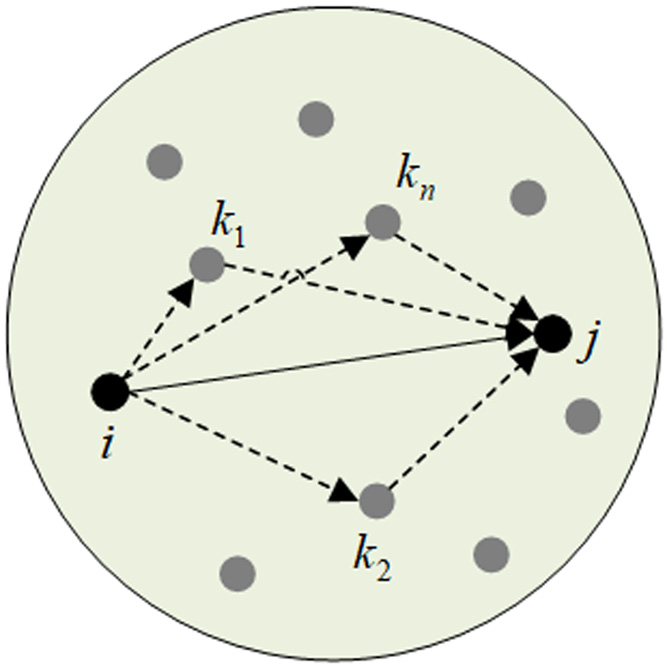 Fig. 2. Direct and indirect trust assessment diagram.
Fig. 2. Direct and indirect trust assessment diagram.
Assuming that there are nodes between node i and node j, can be defined as the direct trust of node i with respect to node . Similarly, can be defined as the direct trust of node to node j with respect to node j:
Comprehensive trust Tij is given by the linear combination of direct trust and indirect trust:
where ω represents the weight of indirect trust. In many trust evaluation models proposed at present, the weight value is set as a fixed value according to the preference of direct trust and indirect trust in different scenarios. Then, when a node in the network fails, the value of trust will change greatly in a certain period of time. Therefore, this paper introduces the coefficient of variation to reflect the change of direct and indirect trust. Then the weight calculation formula is as follows: where V is the coefficient of variation and V = σ/ρ, where σ is the standard deviation of trust and ρ is the average trust. When the coefficient of variation is smaller, it indicates a more stable degree of trust change. For example, if the coefficient of variation increases for a large change in direct trust, then the weight of indirect trust also increases, and a more stable indirect trust is preferred in the weighting.Residual Energy: Sensor nodes are usually severely constrained in terms of their computing power. The energy consumption can be defined in the process of sending and receiving data packets. The residual energy Er of the node can be calculated as:
The energy factor is calculated as , and its value is between [0,1]. Pt is the transmission power, Ds is the size of the data packet, Dr is the packet transmission rate, Pr is the received power, and Ec is the energy consumed by node i to transmit the data packet to node j. Eall is the initial energy and is included in the data packet of the node.
Signal Strength: When the distance between nodes is large, the signal strength is poor and the transmission can be affected by noise and interference, resulting in packet loss. To ensure that the routing protocol can provide stable data transmission, the parameter p is introduced as the reference standard for communication link evaluation in the WSN. It indicates the strength and quality of the received data packets. The node signal strength is calculated based on the TwoRayGround transmission model as:
where Pt is the transmitted power, Gt is the antenna gain of the sending node, Gr is the antenna gain of the receiving node, ht is the height of the transmitting antenna, hr is the height of the receiving antenna, d is the distance between two nodes, and L is the system loss factor.Pheromone Concentration: Once the pheromone concentration influencing factors have been calculated, we can calculate the pheromone concentration H as:
where α is the coefficient of each factor, and .Pheromone update: The ants in the basic ant colony algorithm reach the destination through the path with the most pheromones. If a path is the optimal path to the destination, several ants pass through it, significantly decreasing the energy of the network node on the path, and reducing the life cycle of the entire network. Therefore, when considering pheromone updates, ants must be able to pay attention to the changes in path energy and path length to determine the optimal path. When the energy of different path lengths is the same, the shortest path must be chosen as the optimal path. Considering the minimum energy and the AE of the path nodes, we can effectively balance the energy load of the network and reduce the energy gap between nodes to avoid the death of some of the nodes on a path due to energy exhaustion. The global information update rules of the ant colony algorithm proposed herein are
The ant week model is used as the pheromone local update algorithm model. The improved formula is
where and represent the minimum energy and average energy, respectively, of an ant n passing through the path nodes; Ln denotes the path length taken by an ant n from the source node to the destination node; and Q is a globally set constant.4)ROUTE MAINTENANCE
The pheromone concentration H is updated for each node at intervals of time t. As the message spreads, two trends appear in the link:
- •When the trust of the nodes in a link is relatively stable, most of the messages will pass through the path with the highest trust. Due to the forwarding of several messages, the energy of the nodes along this path decreases. When this happens, the weight assigned to the energy in the calculation of the pheromone concentration H will increase for the nodes with lower energy. Consequently, the H of the low-energy nodes reduces, and other paths with a higher transition probability are selected. Thus, the energy load of the entire network can be balanced, thereby improving the energy efficiency of the network.
- •When the trust of the nodes in a link is unstable, based on the trend of slow increase and decrease in trust, the trust of the node will decrease. The weight of the corresponding trust will increase significantly, thereby reducing the value of H; for example, when a node in a link does not perform the corresponding operation. Subsequently, the nodes with a higher transition probability will be determined. Notably, uncooperative nodes can be determined quickly and the current path can be changed if it contains uncooperative nodes.
B.DATA ENCRYPTION PHASE
To counter external attackers, this paper introduces proxy re-encryption into the wireless network environment. The proxy re-encryption algorithm is introduced in the data encryption phase to provide technical support for data security assurance. The sensor nodes communicate with each other through a multi-hop wireless link, and the intermediate nodes in the network responsible for forwarding are the proxy nodes. These proxy nodes convert the received ciphertext and send it correctly to the destination node, and the specific scheme is designed as follows.
1)PRELIMINARIES
In this section, we provide the necessary preliminary details.
Bilinear Map: G and GT denote two multiplicative cyclic groups with the same prime order q. g is a generator of group G. A bilinear pairing is a bilinear map .
Notation: The notation used in this scheme are
- a.: hash functions, .
- b.: hash functions, .
- c.: hash functions, .
- d.: Key derivation function, .
Protocol: As with most PRE schemes, the protocol has a total of seven phases: Setup, KeyGen, SymKeyGen, Encrypt, ReEncrypt, ReDecrypt, and Decrypt.
2)PROPOSED SCHEMES
This paper gives a data encryption scheme using proxy re-encryption based on a gated secret sharing scheme using Lagrangian polynomials, the security of which relies on the discrete logarithm difficulty problem. The source node encrypts the data information to be transmitted using a symmetric encryption algorithm and later constructs multiple re-encryption keys by polynomial interpolation in the gated secret sharing algorithm, allowing the proxy node to transform the symmetrically encrypted ciphertext of the source node into a ciphertext that can only be decrypted by the private key of the destination node, and the specific scheme design is shown in Fig. 3.
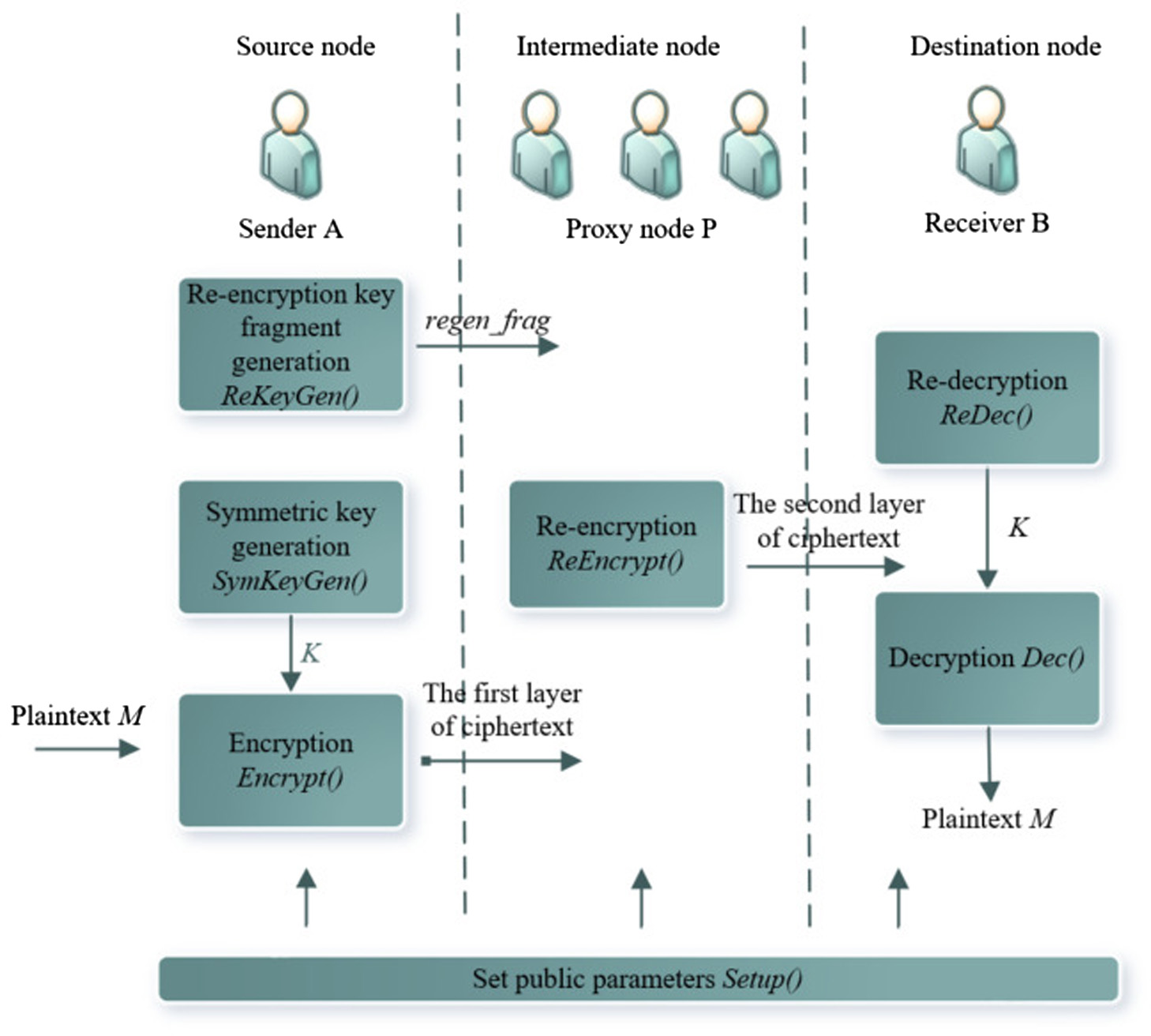 Fig. 3. Proxy re-encryption scheme works.
Fig. 3. Proxy re-encryption scheme works.
Set public parameters: The global public parameter is tuple: . The global common parameters are shared by all the participants in the WSN.
Key generation algorithm: The source node contains its own key pair generation algorithm and a proxy re-encryption key generation algorithm, and also by default both the source and destination nodes have access to each other’s public keys.
- (a)KeyGen(params): randomly select , calculate , and generate a key pair , .
- (b)ReKeyGen: Enter the key , . N fragments (representing the N proxy node), whose threshold is k, which implies that at least k proxy nodes are required to decrypt the proxy re-encryption:
- •Randomly select and calculate .
- •Calculate and , where d is the Diffie–Hellman of s key pair and temporary key pair , the result of the key exchange. This shared key is used to make the re-encryption key of the scheme noninteractive.
- •Randomly select of , where , and calculate . Construct the polynomial , similar to .
- •Select random number , calculate , calculate polynomial , and . Define the re-encryption key fragment as a tuple ,where and are the signatures of the re-encrypted key fragments.
- •Repeat N times and output a set of re-encrypted key fragments .The source node distributes the re-encryption key fragment to each proxy node.
SymKeyGen: When is entered, selecting random number , and calculating ,, and , we will get the tuple . After checking the validity, the symmetric key is calculated through the key derivation function.
Encrypt(K,C,M): The symmetric key K obtained by the SymKeyGen algorithm is used to symmetrically encrypt the message M to obtain encM, and the cipher text is output. This ciphertext is the first layer of the ciphertext and be sent by the source node to each proxy node.
ReEncrypt: After receiving the re-encryption key fragment and the first layer of cipher text, the proxy node re-encrypts the first layer of cipher text. First, the encM in is kept unchanged. Then, calculate and . Finally, the second layer key fragment is output, and the second layer of ciphertext is obtained.
ReDecrypt: The destination node must receive the of k proxies to decrypt the ciphertext.
- •First, enter the private key of destination node and the public key of source node, then we will get from proxy nodes.
- •Calculate , .
- •The following equations are calculated by Lagrangian interpolation according to ,, and finally the symmetric key is output:
Decrypt: The destination node can decrypt encM according to the obtained symmetric key and finally get the message plaintext M.
3)SECURITY ANALYSIS
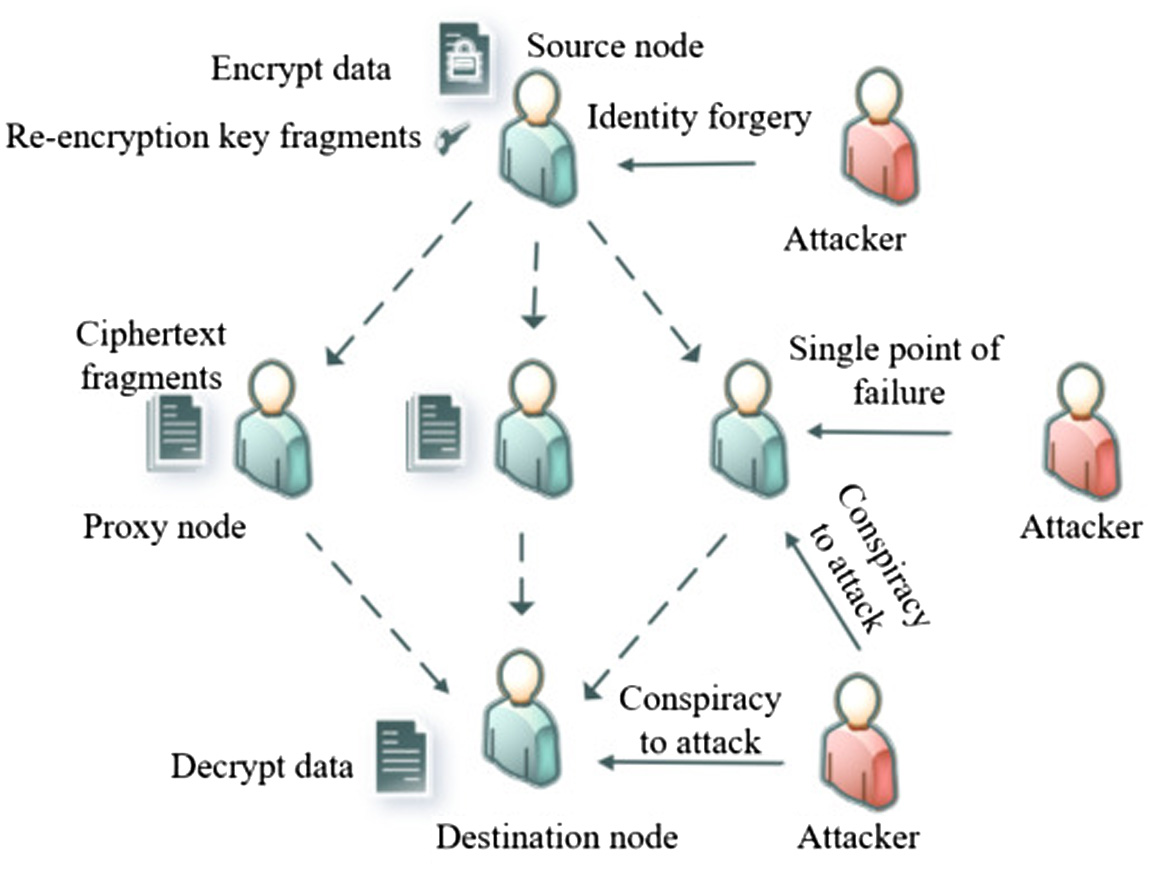
Threat Model: This section defines the threat model of the scenario through the behavior of the nodes involved in data transmission in the network, as shown in Fig. 4.
Source node: The source node in the WSN sends the collected data to the destination node, and we assume that the data sender is honest (i.e., the data is genuine). But, there is a possibility of attackers in the network impersonating the identity of the real data sender, who can encrypt real data and forge fake packet encryptions to contaminate the sensed data.
Destination node: The destination node in the WSN acts as the receiver of the stored and analyzed data. We assume that the data receiver is malicious so that destination nod can launch a conspiracy attack with a proxy node, thus bypassing the restrictions of heavy encryption and compromising the confidentiality of the data.
Proxy node: It is assumed that the proxy nodes are semi-trustworthy, and some of them may eavesdrop on the data content or perform dishonest encryption.
External attacker node: Attackers cannot access to data directly, but they can compromise from within or outside the network.
Security analysis: Based on the threat model presented, the data is encrypted at the source node, then forwarded to the proxy node, and finally received and decrypted by the destination node. There they attack some malicious at any point. They can falsify identity information or even damage the sensor node physically, which can lead to data leakage. With the adoption of the threshold-based proxy re-encryption scheme in this chapter, the problems posed by the threat model can be effectively avoided.
Identity forgery: The problem of identity forgery is a hidden problem caused by the source node in the threat model. Since the public key encryption algorithm allows any node to encrypt the plaintext of a message with the public key of source node, it is possible for an attacker to forge an identity and impersonate the source node to encrypt the data. To prevent this, we uses a digital signature to verify the source node’s identity to the data recipient. The digital signature of the scheme is stored in a fragment of the re-encryption key , and it cannot be sent directly to the destination node for verification. Therefore, we avoid the leakage of the identity of the source node due to monitoring. The destination node takes the digital signature as part of the shared data and cannot verify the signature until the ciphertext has been decrypted.
Conspiracy attacking: If the proxy node collude with a destination node, it will choose to leak the re-encryption key directly to the destination node who can decrypt the data at will without any constraints. Our method use a threshold-based proxy re-encryption scheme, in which the re-encryption key is constructed into multiple key fragments , then distributed to multiple proxy nodes in the network. Such an approach disperses trust among multiple proxy nodes, and if destination node wants to launch a conspiracy attack, it needs to collude with at least the number of k proxy node, which is equivalent to solving the threshold secret sharing problem. As we know, it is computationally impossible, so our method increases the difficulty of the conspiracy attack greatly.
Single point of failure: Due to the WSN is in the middle of an open network, there are the possibility of sensor nodes being deployed in enemy territory. When a node is captured by an enemy, there is the potential for the node to be compromised. When a particular proxy node is attacked, it will disrupt the process of encrypting the network data transmission. Since our method uses a threshold-based proxy re-encryption scheme with multiple proxy nodes, the destination node only needs to obtain the number of k fragment of the key to decrypt. So it allows the data encryption process to remain intact even if some of the proxy nodes fail.
IV.SIMULATION SETUP AND EXPERIMENTAL RESULTS
This section describes the experimental evaluation of ACOTPRE. The simulation model, performance metrics, and comparative analysis are described in this section.
A.SIMULATION MODEL
The performance of the proposed scheme was tested using Network Simulator version 3.27. A total of 50 nodes were randomly distributed in an area of 1000 m × 1000 m, and the transmission distance was fixed at 100 m. The source node and the target node were randomly selected from the network. Table I shows the simulation configuration in experiments.
Table I. Simulation parameters.
| Parameters | Value |
|---|---|
| Range of simulation | 1000 m × 1000 m |
| Number of nodes | 50 |
| Transmitting power | 24·75 mW |
| Receiving power | 13·5 mW |
| Packet transmission rate | 40 kbps |
| Packet size | 100bit |
| Initial energy of the node | 1 J |
| Range of node communication | 100 m |
B.EXPERIMENTAL RESULTS
The PDR, EED, and ARE were used to evaluate the proposed scheme.
1)PERFORMANCE INDICATORS
Packet delivery ratio (PDR): The efficiency of any routing algorithm can be analyzed by estimating the number of data packets communicated to sink node. So the PDR is the ratio of the number of successfully received data packets to the total number of data packets sent:
where Nr is the number of data packets successfully received by the target node and Ns is the total number of data packets sent by the source node. End-to-end delay (EED): The EED represents the time taken by a data packet to travel from the source node to the destination node. The delay should be less to achieve effective routing: where is the time at which the destination node receives the data packet and is the time at which the source node sends the data packet. The total number of nodes in the network is n, and nN is the total number of data messages. Average Residual Energy (ARE): ARE is obtained by calculating the energy level consumed by each node at the end of the simulation (i.e., packet transmission). In a WSN, every data packet sent to the sink node consumes a certain amount of energy. The energy consumption of the network can be determined by calculating the ARE remaining in the network. The larger the ARE remaining in the network, the lesser the ARE consumed and the longer the life cycle of the network:where Ei is the total number of nodes in the network and n is the energy remaining in each node.2)PERFORMANCE ANALYSIS
This section compares the ACOTPRE with other existing methods, namely the AODV protocol and Refine Trust Energy (ReTE)-AODV, in terms of PDR, EED, and ARE.
PDR: Fig. 5 depicts the variation in PDR with the number of nodes, considering the AODV, ReTE-AODV, and ACOTPRE. It can be found that as the number of nodes increases, the PDR gradually decreases. This result is due to the more the number of nodes, the higher the network congestion, causing more link failures. However, the PDR for ACOTPRE increases considerably as compared to both protocols. When the number of nodes is kept constant at same, the PDR of proposed scheme is approximately increased by 19% as that of ReTE-AODV. From the Fig. 5, it is clear that by increasing the node count, the gap of PDR between the ACOTPRE and AODV has gradually increased, from an increase of 22% to 124%.
 Fig. 5. Packet delivery ratio comparison with different nodes count.
Fig. 5. Packet delivery ratio comparison with different nodes count.
EED: From Fig. 6, it is obvious that EED increases with increase in the number of nodes. We notice that ACOTPRE has lower delay than AODV, then the delay is reduced by 0·18 s on average. The reason is that the classic AODV algorithm does not use trust model, while ReTE-AODV and our method are both trust-based algorithms to improve performance by eliminating malicious and selfish nodes in routing and reducing end-to-end delay. Since nodes have limited memory, ACOTPRE requires larger computing requirements but saves some storage. Then the ACOTPRE showcases EED slightly higher than that of ReTE-AODV with better reliability. The average EED of the proposed scheme was found to be 0·998 s, whereas ReTE-AODV exhibited an average EED of 0·814 s.
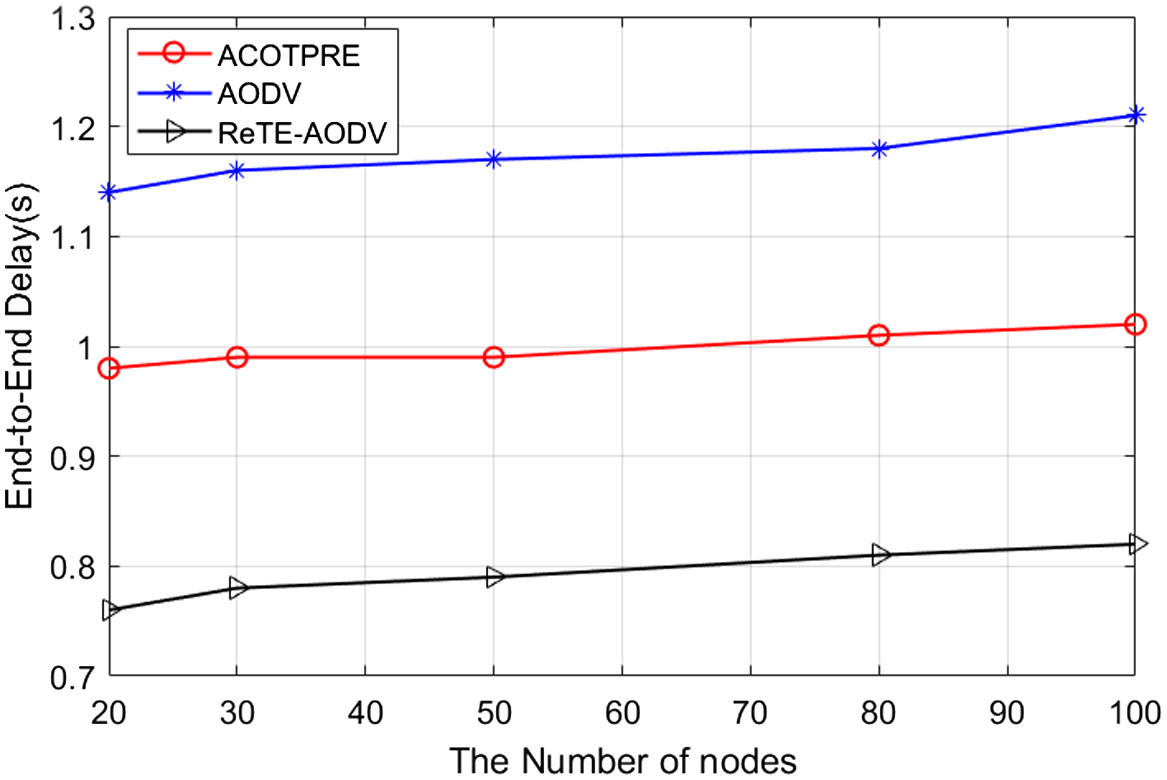 Fig. 6. End-to-end delay comparison with different nodes count.
Fig. 6. End-to-end delay comparison with different nodes count.
ARE: Fig. 7 shows the ARE change of nodes corresponding to the ACOTPRE, AODV, and ReTE-AODV for a fixed number of network nodes of 50, which also compares this paper’s ACOTPRE scheme (i.e., without adding proxy re-encryption). The ACOTPRE consumes more energy than the AODV. However, ACOTPRE is more secure, and its high energy consumption does not affect the selection of transmission path. The average residual energy of ACOTPRE is higher than RETE-AODV, because when ants choose the optimal path, the pheromone concentration update strategy is based on the energy in the network so that it can balance the energy consumption of the network. Although the ACOTPRE contains proxy re-encryption based on threshold secret sharing, which requires the source and destination nodes to compute polynomial interpolation, the other proxy nodes only perform two exponential operations, so the overall computational energy consumption of the network is not significantly increased.
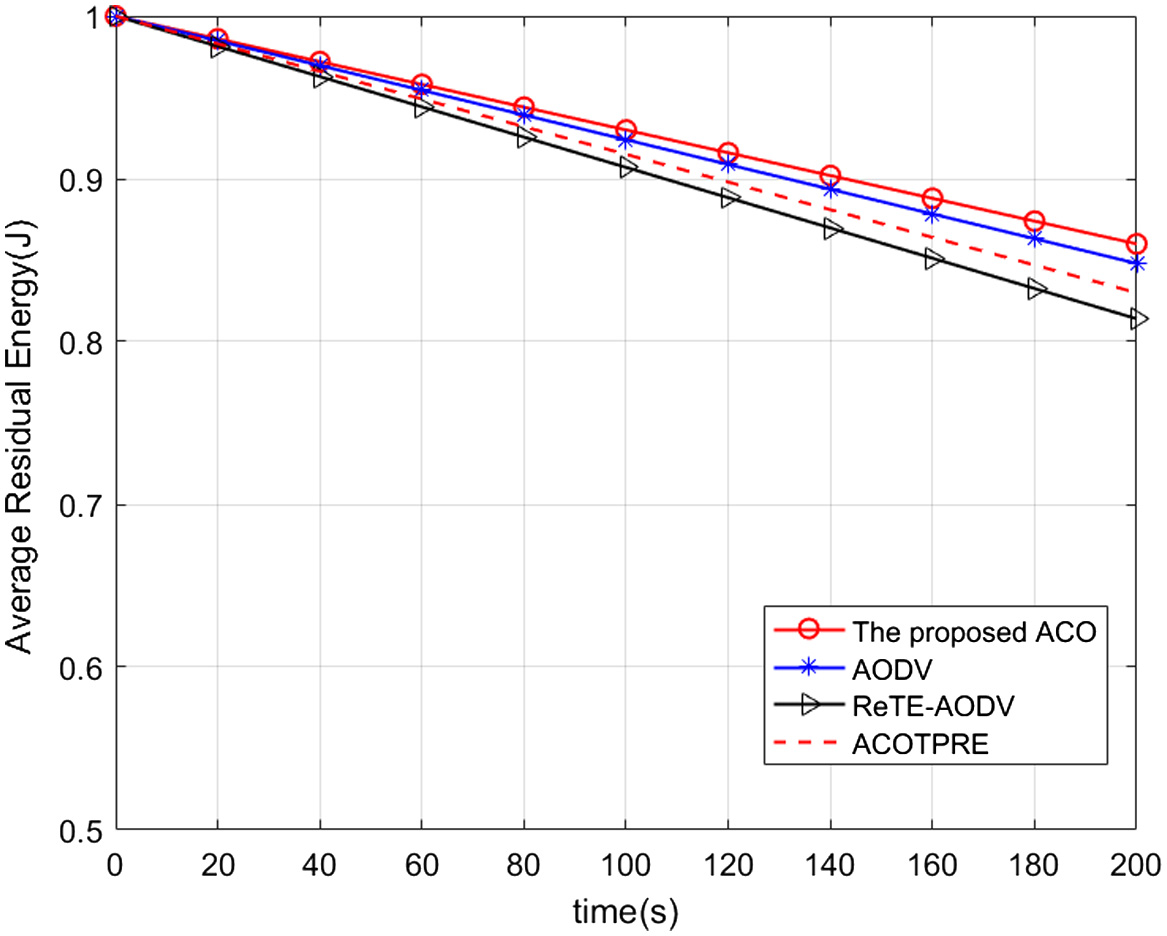 Fig. 7. Average energy remained comparison with different nodes count.
Fig. 7. Average energy remained comparison with different nodes count.
C.SYSTEM SECURITY
This paper proposes the deployment of an AOCTPRE security strategy in the data transmission path selection phase and data encryption phase. By establishing a trust assessment model between nodes in the path selection phase, the number and content of data packets are identified as direct trust indicators. WSNs can defend against most attacks from internal attacker nodes effectively that incorporate a trust mechanism. This security mechanism is a passive defense mechanism, which cannot identify and remove external attackers disguised as normal nodes. And its defense capability has certain limitations. Therefore, in the data encryption phase, a threshold-based proxy re-encryption scheme is constructed to build a defense system that organically combines active defense and passive defense, so as to achieve security protection for the whole network.
V.CONCLUSION
In this paper, we proposed a data transmission mechanism in WSN that enforces both security and performance. The proposed mechanism is based on the ACO during a path selection phase and the threshold PRE during a data encryption phase. ACOTPRE solves the data transmission path problem by constructing a new pheromone factor that includes trust, energy, and signal strength. A threshold proxy re-encryption method is used to solve security issues related to data encryption. The security of our scheme relies on the concept of the trust model and threshold secret sharing to resist internal attacks and external attacks. We have confirmed the validity and performance of our model via simulation studies. In our future work, we plan to conduct a more in-depth examination about computational complexity and network delay.